Xafekopy
Original Issue Date:-
September 11, 2017
Virus Type:-
Trojan
Severity:-
High
Aliases: Trojan-Clicker.AndroidOS.Xafekopy
Description
It has been reported that a malware named as “Xafekopy” affecting android devices was spreading. The malware is capable of causing financial losses to the customer via WAP billing. This Trojan is distributed via ads masquerading as useful apps like battery optimizers etc. Upon installation, the Trojan uses JS files to click on buttons on web-pages containing WAP billing and subscribes the affected mobile phone to many services without users knowledge. Trojan first turns off the WiFi and turning on the mobile Internet because WAP-billing works only through mobile Internet and open a URL that redirects to the page with WAP-billing.
WAP (Wireless Application Protocol) sites, is a form of mobile payment, which charges directly to the user's mobile phone bill. It is an alternative payment mechanism to debit or credit cards and premium SMS for billing. During the process, it does not required the debit/credit cards details or username and password for the payment option. The malware capable of bypassing the “captcha” authorization designed to protect users by confirming a human is performing the action.
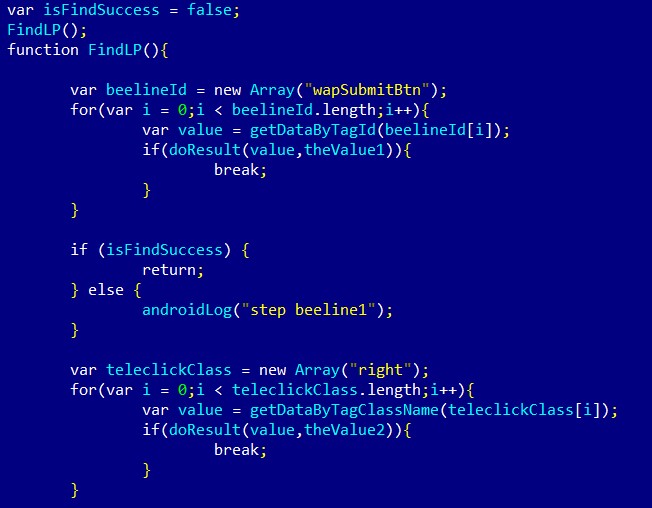
Part of JS files used by Trojan-Clicker.AndroidOS.Xafekopy to click on buttons
Source: SecureList
This Trojan distributed via useful apps, mostly as battery optimizers. After installation, it loads a malicious library. This library decrypts and loads files from the assets folder of the installation package. These files decrypt and load another file from the assets folder, which contains the main malicious functionality. It decrypts (yep, decryption again) JS files. Using these JS files it can bypass captcha forms and click on web-pages with WAP billing. By doing so, it steals money from a user’s mobile accounts (billing). It can also click on some ad pages to make money from ads.
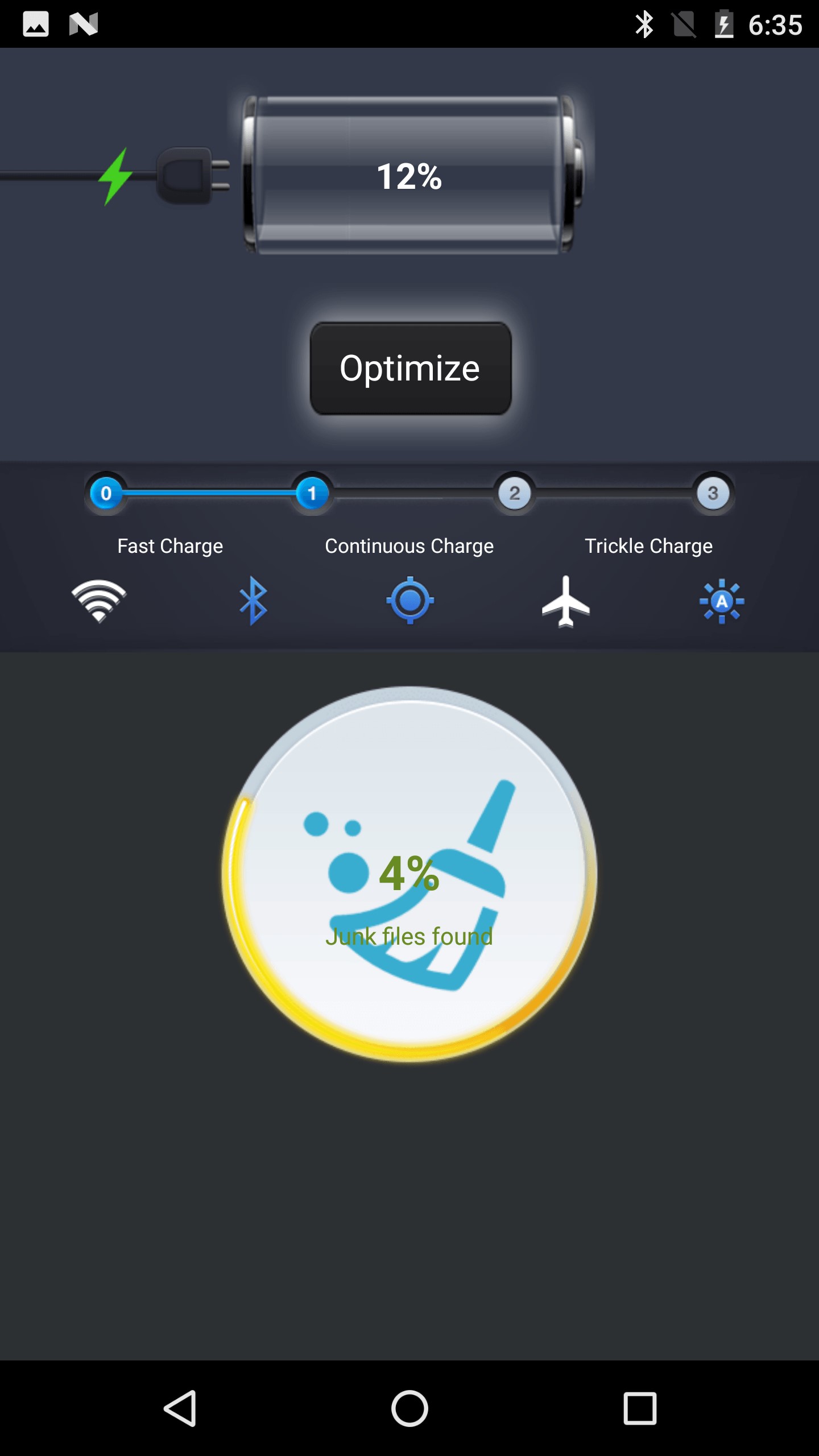
While users see a “Battery Master” interface the Trojan is trying to steal money
Source: SecureList
Indicators of Compromise (IoC)
MD5 Checksum of some malicious app files:
- F3D2FEBBF356E968C7310EC182EE9CE0
- 9E492A6FB926E1338DADC32463196288
- A93D3C727B970082C682895FEA4DB77B
- 66FE79BEE25A92462A565FD7ED8A03B4
- AEAE6BFDD18712637852C6D824955859
- DA07419994E65538659CD32BF9D18D8A
Countermeasures:
- Do not download and install applications from untrusted sources. Install applications downloaded from reputed application market only.
- Do not check "Untrusted Sources" checkbox to install side loaded apps.
- Do not click on banners or pop-up or ads notifications on android device.
- Before installing any app on Android mobile, read the app's terms and conditions, specifically permissions required.
- Install Android updates and patches as and when available from Android device vendors
- Install and maintain updated mobile security/antivirus solution
- If any of the malicious apps mentioned in the above Indicators of Compromise (IoC) are installed, then uninstall the same.
- Refer to security tips for mobile Phone: http://www.cyberswachhtakendra.gov.in/documents/Mobile_phone_Security.pdf
- Follow CERT-In Advisory Smartphone Security (CIAD-2017-0040)
- Enable 2-factor authentication for your Google/other accounts.
- Run a full system scan on device with mobile security solution or mobile antivirus solution.
- Exercise caution while visiting trusted/untrusted sites for clicking links.
- Users are advised to use device encryption or encrypting external SD card feature available with most of the android OS
- Users are advised to keep an eye on Data usage (application wise usage also) and unusual increase in mobile bills
- Users are advised to keep an eye on device battery usage (application wise usage also)
- Load Flash content on demand
- Use Android Device Manager to locate, remotely lock, or erase your device
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
- Make a practice of taking regular backup of android device
References
- https://securelist.com/wap-billing-trojan-clickers-on-rise/81576/
- https://www.theregister.co.uk/2017/08/24/wap_scam_mobile_trojans/
- http://www.deccanchronicle.com/technology/in-other-news/040917/mobile-trojans-steal-users-money-through-wap-billing-services.html
- CERT-In Advisory Smartphone Security (CIAD-2017-0040)


