Linux: Lilu/Lilocked Ransomware
Original Issue Date:-
September 20, 2019
Virus Type:- Ransomware
Severity:-
High
It has been reported that the malware named as lilu/Lilocked having ransomware capabalities targeting linux machines is spreading. The infection vector used by the ransomware is currently unknown. However some of the functionalities of the malware is as follows:
- Target linux servers and gain their root access.
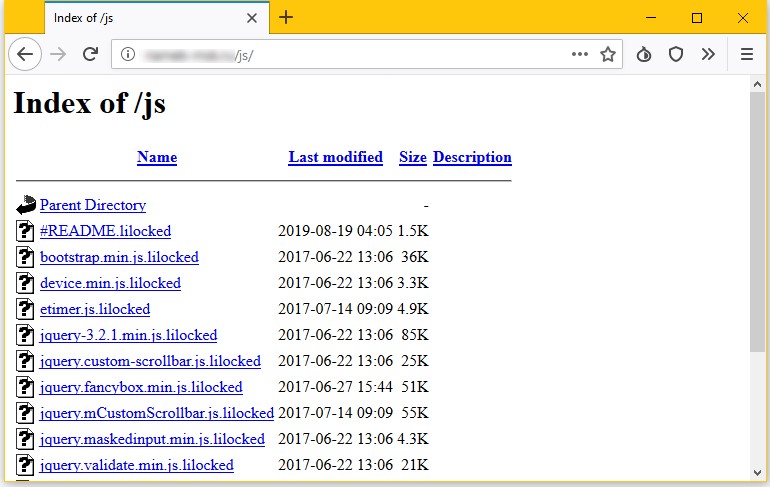
- Locked files after encryption with “.lilocked” extension.
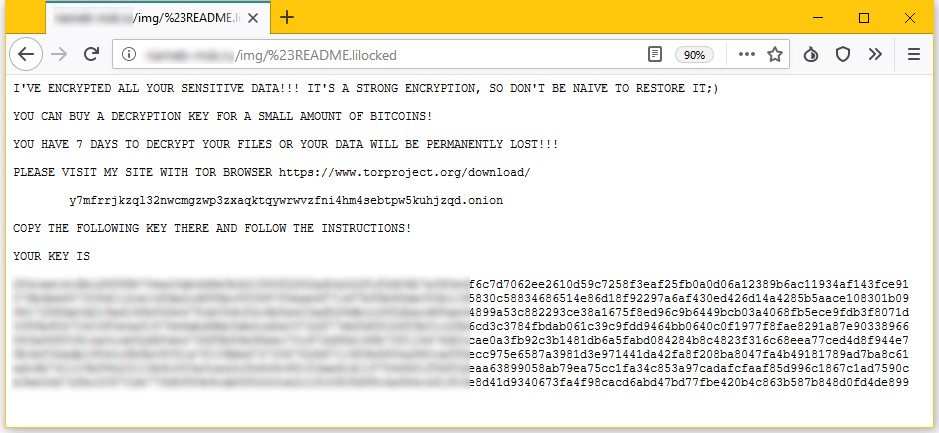
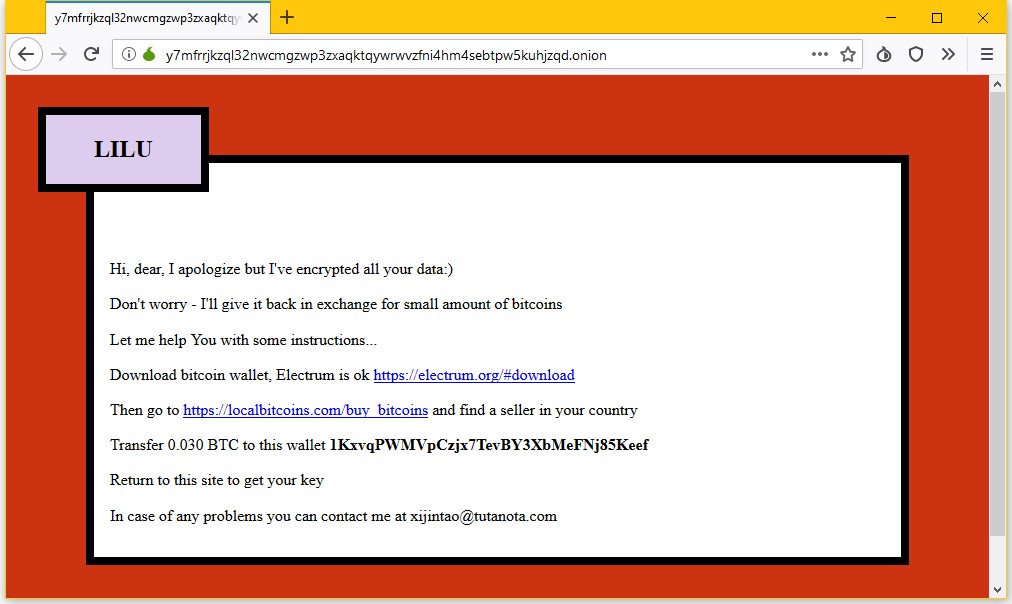
- Shows ransomware note ot the victim and demands 0.03 bitcoin or $325 in the Electrum Wallet for decryption key.
- It encrypts or targets only specific file types such as HTML, SHTML, JS, CSS, PHP, INI and other image file formats and does not encrypts or effect system files.
Files encrypted by the ransomware are shown below:
Ransomware note shown to the user is shown below:
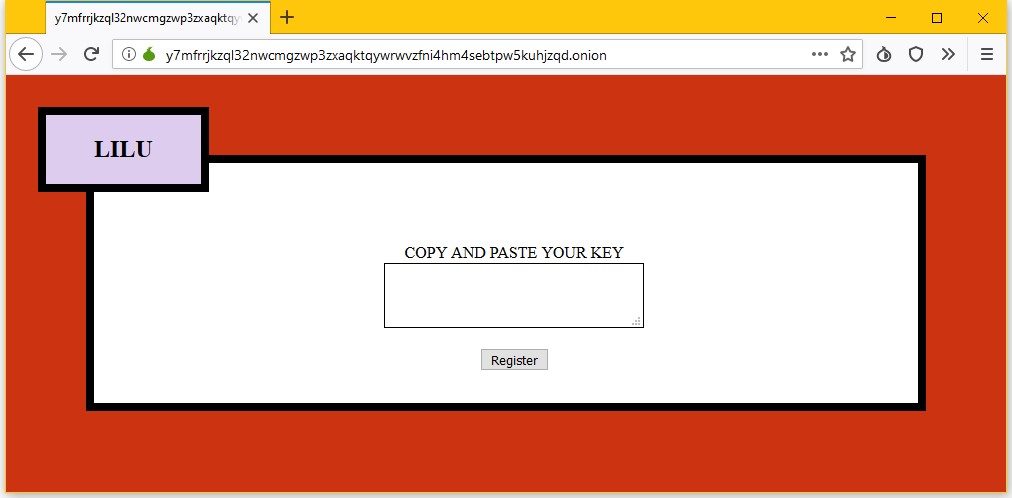
Portal demanding ransomware from the victim is shown below:
Best Practices
- Users are advised to disable their RDP if not in use, if required it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser.
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Change default credentials at device startup and ensure that passwords meet the minimum complexity.
- Control access to the devices with Access List
- Configure devices to "lock" or log out and require a user to re-authenticate if left unattended
- Identify systems with default passwords and implement abovementioned measures. Some the systems that need to examined are Routers, switches, web applications and administrative web interfaces, ICS systems, Telnet and SSH interfaces
- Implement account lockout policies to reduce the risk of brute forcing attacks.
- Telnet and SSH should be disabled on device if there is no requirement of remote management
- Configure VPN and SSH to access device if remote access is required.
- Configure certificate based authentication for telnet client for remote management of devices
- Implement Egress and Ingress filtering at router level.
- Report suspicious entries in Routers to your Internet Service Provider
- Keep up to date Antivirus on the computer system
- Unnecessary port and services should be stopped and closed.
- Enable and monitor perimeter device logs to detect scan attempts towards critical devices/systems
References:
- https://securityintelligence.com/news/lilocked-ransomware-infects-thousands-of-linux-servers-to-encrypt-files/
- https://www.zdnet.com/article/thousands-of-servers-infected-with-new-lilocked-lilu-ransomware/
- https://www.notebookcheck.net/Lilu-Lilocked-ransomware-has-now-infected-thousands-of-Linux-servers.434547.0.html
- https://www.bleepingcomputer.com/news/security/lilocked-ransomware-actively-targeting-servers-and-web-sites/
- https://fossbytes.com/lilocked-ransomware-infected-linux-servers/


