HiddenWasp Linux Malware
Original Issue Date:-
June 06, 2019
Virus Type:-
Trojan
Severity:-
High
It has been observed that a new malware named as “HiddenWasp” targeting Linux operating systems is spreading. The malware focuses primarily on gaining remote access of the infected hosts making it different from other Linux malwares which aims crypto-mining or DDoS activity. The infection vector used by the malware is not known. The malware is capable of performing the following functions:
- Gaining remote access to the infected machine.
- Evade detection from variety of antivirus solutions.
- Uses malicious code from other known malwares namely Azael Rootkit and Mirai.
- Update existing versions of HiddenWasp on the compromised machine
- Make network connections to download other malwares.
- Make use of rootkits, Trojan implants and creation of ftp user account to maintain persistence in the system.
The malware is a combined package of various open source malwares such as an initial deployment script for downloading other malwares along with updating existing threats, a rootkit using Mirai code to hook into several functions and a Trojan having features of Azael rootkit that worked with the rootkit to remain operational. Also, similarities have been found in the HiddenWasp malware and other Linux malware named as Winnti malware.
Working
Malware start its activities by execution of the initial deployment script which contains a code to create a user named as “sftp” on the compromised system with hardcoded password to maintain attacker’s access to infected machine even after the malware detection and cleanup. It is shown as below:
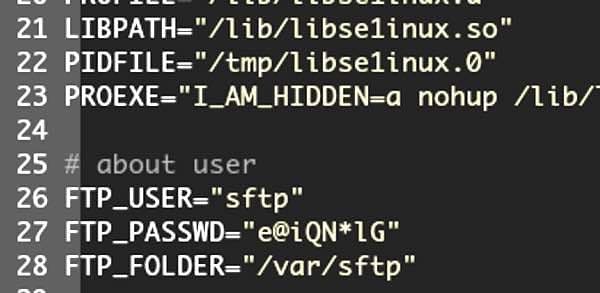
Source: Intezer
Thereafter the malware connects to remote server to download a tar file containing a full malware configuration package and then perform its other activities. The working of the malware is as follows:
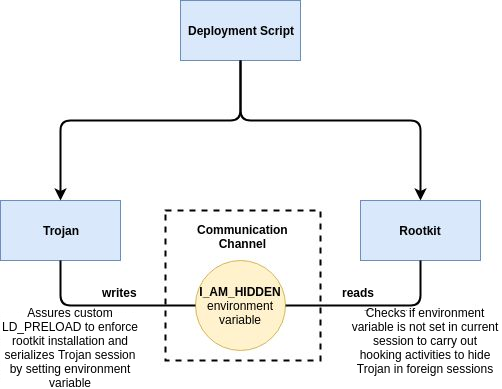
Source: Intezer
Indicators of Compromise:
Command and Control server:
- 103[.]206[.]123[.]13
- 103[.]206[.]122[.]245
URLs downloading malicious script:
- hxxp://103.206.xx.xx/system.tar.gz
- hxxp:// 103.206.xx.xx /configUpdate.tar.gz
- hxxp:// 103.206.xx.xx /configUpdate-32.tar.gz
File Hashes
- e9e2e84ed423bfc8e82eb434cede5c9568ab44e7af410a85e5d5eb24b1e622e3
- f321685342fa373c33eb9479176a086a1c56c90a1826a0aef3450809ffc01e5d
- d66bbbccd19587e67632585d0ac944e34e4d5fa2b9f3bb3f900f517c7bbf518b
- 0fe1248ecab199bee383cef69f2de77d33b269ad1664127b366a4e745b1199c8
- 2ea291aeb0905c31716fe5e39ff111724a3c461e3029830d2bfa77c1b3656fc0
- d596acc70426a16760a2b2cc78ca2cc65c5a23bb79316627c0b2e16489bf86c0
- 609bbf4ccc2cb0fcbe0d5891eea7d97a05a0b29431c468bf3badd83fc4414578
- 8e3b92e49447a67ed32b3afadbc24c51975ff22acbd0cf8090b078c0a4a7b53d
- f38ab11c28e944536e00ca14954df5f4d08c1222811fef49baded5009bbbc9a2
- 8914fd1cfade5059e626be90f18972ec963bbed75101c7fbf4a88a6da2bc671b
Best Practices and Recommendations:
- Check for the indicators of compromise associated with the malware and block command and control domain and IP addresses at security perimeter devices.
- Execute YARA rules against in-memory artifacts in order to be able to detect trojan implants.
- To check if your system is infected, search for “ld.so” files — if any of the files do not contain the string ‘/etc/ld.so.preload’, your system may be compromised. This is because the Trojan implant will attempt to patch instances of ld.so in order to enforce the LD_PRELOAD mechanism from arbitrary locations.
- Restrict Web Management Interface access of IoT devices to authorized users only and change default username/passwords
- Always change Default login credentials before deployment in production.
- Change default credentials at device startup and ensure that passwords meet the minimum complexity.
- Disable Universal Plug and Play (UPnP) on IoT devices unless absolutely required.
- Users should be aware of the installed devices and their capabilities. If a device comes with a default password or an open Wi-Fi connection, users should change the password and only allow it to operate on a home network with a secured Wi-Fi router.
- Control access to the devices with Access List
- Configure devices to "lock" or log out and require a user to re-authenticate if left unattended
- Identify systems with default passwords and implement abovementioned measures. Some the systems that need to examined are Routers, switches, web applications and administrative web interfaces, ICS systems, Telnet and SSH interfaces
- Implement account lockout policies to reduce the risk of brute forcing attacks.
- Telnet and SSH should be disabled on device if there is no requirement of remote management
- Configure VPN and SSH to access device if remote access is required.
- Configure certificate based authentication for telnet client for remote management of devices
- Implement Egress and Ingress filtering at router level.
- Report suspicious entries in Routers to your Internet Service Provider
- Keep up to date Antivirus on the computer system
- Keep up-to-date on patches and fixes on the IoT devices, operating system and applications.
- Unnecessary port and services should be stopped and closed.
- Logging must be enabled on the device to log all the activities.
- Enable and monitor perimeter device logs to detect scan attempts towards critical devices/systems
References:
- https://www.intezer.com/blog-hiddenwasp-malware-targeting-linux-systems/
- https://threatpost.com/new-linux-malware-hiddenwasp-borrows-from-mirai-azazel/145209/
- https://www.informationsecuritybuzz.com/expert-comments/meet-hiddenwasp-the-new-malware-strain-targeting-linux-systems/
- https://securityintelligence.com/news/new-hiddenwasp-linux-malware-focused-solely-on-achieving-targeted-remote-control/
- https://koddos.net/blog/linux-targeted-by-chinese-malware-dubbed-hiddenwasp/
- https://www.tripwire.com/state-of-security/security-data-protection/hiddenwasp-malware-seizes-control-of-linux-systems/


