Android Malware Gooligan/Ghost Push
Original Issue Date:- December 06, 2016
Updated on:- March 12, 2018
Virus Type:- Trojan/ Rootkit
Severity:- Medium
It has been reported that the malware named Gooligan aka Ghost Push, Shedun, SnapPea, Xinyinhe, is infecting vulnerable android devices and compromising large number of google accounts. Gooligan pretends to be a legitimate Android App and trick users to install the app which results in infecting the Android device. Other infection mechanism used by the malware is use of phishing mails, SMS or other messaging services containing malicious link to download Gooligan-infected app from untrusted app. Once the device is compromised, it will then install several other unwanted apps which cannot be removed easily. These apps remain persistent on device even after performing factory reset of the phone.
It has also been reported that the Gooligan malware code is found is in dozens of legitimate-looking apps found on third-party Android app stores. These Android app stores are an alternative to Google Play offering many free apps and free versions of paid apps. The security of these alternative Android app stores and offered apps are not verified always.
Upon installing an infected app, it sends affected device information to the Command and Control (C&C) server. Later, Gooligan downloads a rootkit from C&C server which takes advantage of multiple Android version 4 and 5 exploits including VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153) vulnerabilities. Along with this it also exploits ELF(Executable Link File) vulnerability. Exploitation of these vulnerabilities leads to the successful rooting of the android device allowing attacker to have full control of the infected device.
The malware is capable of performing the following functions:
- Install adware to generate revenue.
- Install apps from Google play and rate them to raise their reputation.
- Slowdowns the compromised device performance
- Degrades battery life of the infected device.
- Excessive use of phone’s storage due to installation of unwanted apps unknowingly.
- Excessive data usage.
- Capable of injecting code into running Google Play and google mobile services to mimic users behavior and avoid detection
- Notifications regarding the stealing of account credentials of the infected device.
- Steal authentication tokens from the infected device and attempts to gain access to user’s sensitive data from synchronized accounts, google drives, G suite, Google Photos, Google Docs, etc.
- Capable of rooting the compromised device.
- Make network connections to download further malware and send stolen information.
The malware life cycle depicting its initial source of infection and its later impacts is shown below:
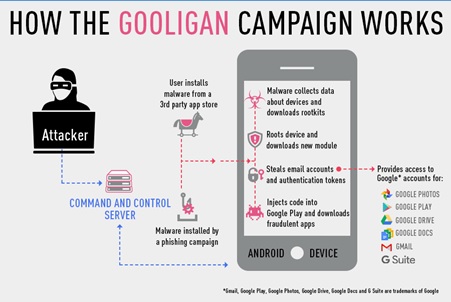
Source: Checkpoint
One of the fraudulent app installed by the malware is shown below:
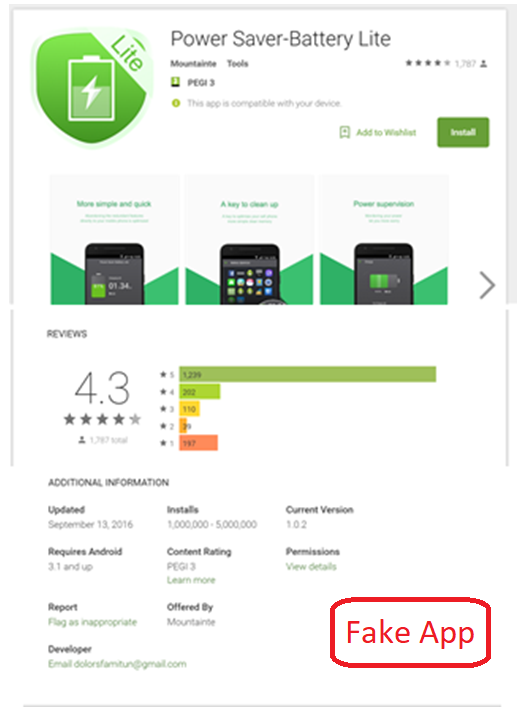
Note: Android phone users may check their account for infection with “Gooligan” at https://gooligan.checkpoint.com/.
Indicators of compromise:
List of malicious apps infected by Googligan:
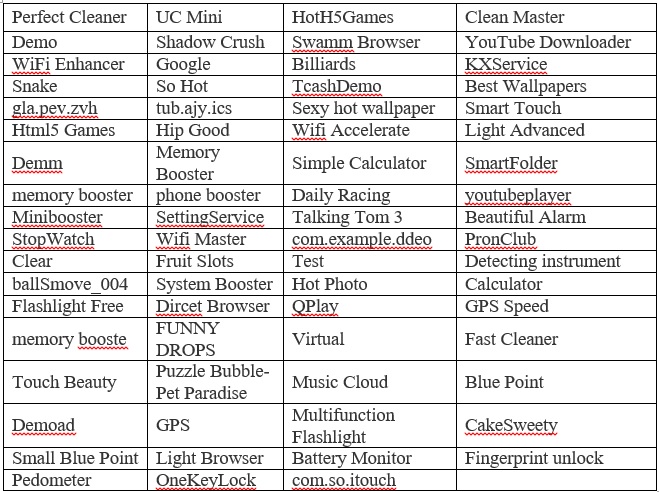
Users are requested to check the installed apps in their respective devices. If any of the above listed apps are found kindly go to the countermeasures section and take the appropriate prevention or cleaning measure.
List of command and control servers contacted by malicious apps:
- api2[dot]appsolo[dot]net
- sys[dot]aedxdrcb[dot]com
- api[dot]aedxdrcb[dot]com
- sys[dot]syllyq1n[dot]com
- sys[dot]hdyfhpoi[dot]com
List of malicious binaries downloaded by Gooligan:
- hxxp://down.cmgkiwdwcom/thinking/group/pl4y_3
- hxxp://down.akocdn.com/onemain/maink.apk
- hxxp://106.186.17.81/rootmasterdemo1128_524.apk
- hxxp://down.vcrlwlen.com/thinking/group/rt1018_648.apk
Countermeasures:
- Scan the suspected device with antivirus solutions to detect and clean infections.
- Disable the account synchronization option in the infected device
- Log out of all the synchronized accounts such as Gmail, Facebook, etc and changed their password using a clean system. Also enable 2-factor authentication mechanism for additional security.
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages].Install applications downloaded from reputed application market only.
- Prior to downloading / installing apps on android devices (even from Google Play Store):
- Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- Do not check "Untrusted Sources" checkbox to install side loaded apps.
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
- Make a practice of taking regular backup of android device.
- Try to clean the infection using factory resets option, if it does not work then go for firmware reflashing to install the fresh operating system on the mobile device. Before reflashing take backup of your important information such as contacts, messages, images etc. to external device.
- Perform the reflashing of all other devices for which these accounts are synchronized.
- Do not click on banners or pop¬up or ads notifications.
- Turn on 2-factor authentication for your Google/other account.
- Run a full system scan on device with mobile security solution or mobile antivirus solution.
- Exercise caution while visiting trusted/untrusted sites for clicking links.
- Install Android updates and patches as and when available from Android device vendors Install and maintain updated mobile security/antivirus solution.
- Users are advised to use device encryption or encrypting external SD card feature available with most of the android OS.
- Users are advised to keep an eye on Data usage (application wise usage also) and unusual increase in mobile bills.
- Users are advised to keep an eye on device battery usage (application wise usage also).
- Load Flash content on demand.
- Use Android Device Manager to locate, remotely lock, or erase your device.
- Refer to security tips for mobile Phone:
http://www.cyberswachhtakendra.gov.in/documents/Mobile_phone_Security.pdf
References
- http://blog.checkpoint.com/2016/11/30/1-million-google-accounts-breached-gooligan/
- https://gooligan.checkpoint.com/
- https://plus.google.com/+AdrianLudwig/posts/GXzJ8vaAFsi
- http://www.cmcm.com/blog/en/security/2015-09-18/799.html
- http://www.cmcm.com/blog/en/security/2016-10-14/1031.html
- https://www.fireeye.com/blog/threat-research/2015/09/guaranteed_clicksm.html
- http://blog.trendmicro.com/trendlabs-security-intelligence/new-ghost-push-variants-sport-guard-code-alware-creator-published-over-600-bad-android-apps/
- http://www.forbes.com/sites/thomasbrewster/2016/11/30/gooligan-android-malware-1m-google-account-breaches-check-point-finds/#503ede31470d
- https://www.helpnetsecurity.com/2016/10/18/ghost-push-trojan/
- http://www.androidauthority.com/ghost-push-malware-root-apps-fix-648735/
- https://blog.avast.com/how-to-protect-your-android-device-from-ghost-push


