Emotet Trojan
Original Issue Date:-
June 26, 2018
Virus Type:-
Trojan
Severity:-
Medium
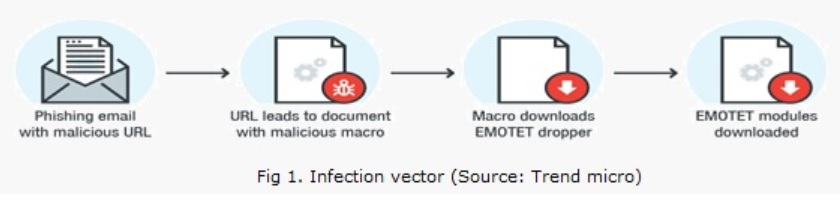
Emotet is banking Trojan which stole the sensitive information from the victim computer. The modes of spreading is unscrupulous phishing emails with malicious attachments or links pointing to malicious documents. Once emotet infect the victim system, it starts building the connection with its C2 server and send all the sensitive data, credentials to the attacker controlled C2 server[s].
Malicious activity:-
- Once victim open the malicious document, it ask for enabling the macro, which will invoke power shell to execute a script present in doc file to download the Emotet from the c2 server.
- After Emotet downloaded, it checks whether it is running in sandboxing environment or not. If it finds that it is running in a sandbox then it will not proceed further, else it will execute further.
- Now emotet act as dropper and download other banking malware names as Zeus Panda banker, Trickbot or Iced ID on the victim machine.
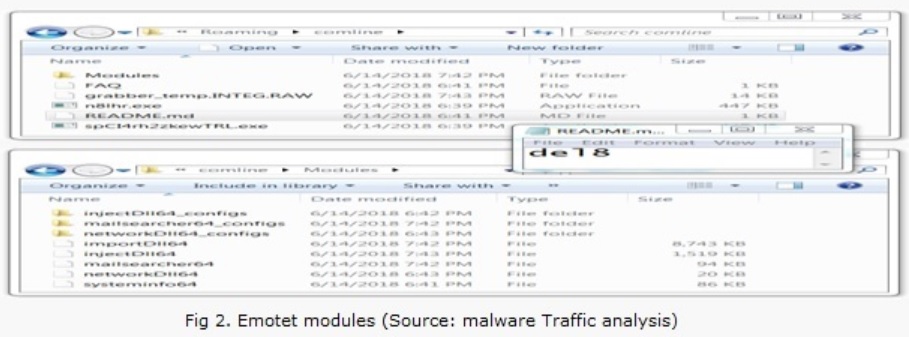
- Emotet also download the different module for performing malicious activities like Banking module for performing authorized transaction, Distributed denial of service (DDoS) module, Spam module for propagation across the network, Email client info stealer module, Browser info stealer module, Personal Storage Table (PST) info stealer module as shown in figure2.
- Finally Emotet start performing malicious activity based upon the module it download like performing authorized transaction, stealing victim credentials, communication with C2 etc. Emotet maintains its persistence via changing the registry Run key.
Indicators of Compromise:
Countermeasures and Best practices
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Restrict execution of PowerShell /WSCRIPT in enterprise environment Ensure installation and use of latest version (currently v5.0) of PowerShell, with enhanced logging enabled. Script block logging, and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
Reference:https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html - Enabled Windows Defender Application Guard with designated the trusted sites as whitelisted, so that rest all sites will be open in container to block the access to memory, local storage, other installed applications or any other resources of interest to the attacker.
- Enabled Windows Defender Credential Guard, User Account Control feature to protecting from credential theft attacks, blocking of the automatic installation of unauthorized apps and run the apps ,tasks in non-administrative accounts unless administrator specifies.
- Keep up-to-date Antivirus and Antispyware signatures. Keep checking the traffic flow from your system at above mentioned IP, domain regularly
- Follow safe practices when browsing the web.
References:


