WastedLocker Ransomware
Original Issue Date:- July 16, 2020
Virus Type:- Ransomware
Severity:- Medium
It has been reported that a new ransomware, named as “WastedLocker” is spreading. The attack is mainly focused on U.S. located organizations of various industries including manufacturing, media, IT, healthcare and many more. The ransomware attack is attributed to infamous cybercriminal outfit “Evil Corp” that was earlier linked to some other dreadful cyber-attacks also.
Infection Mechanism:
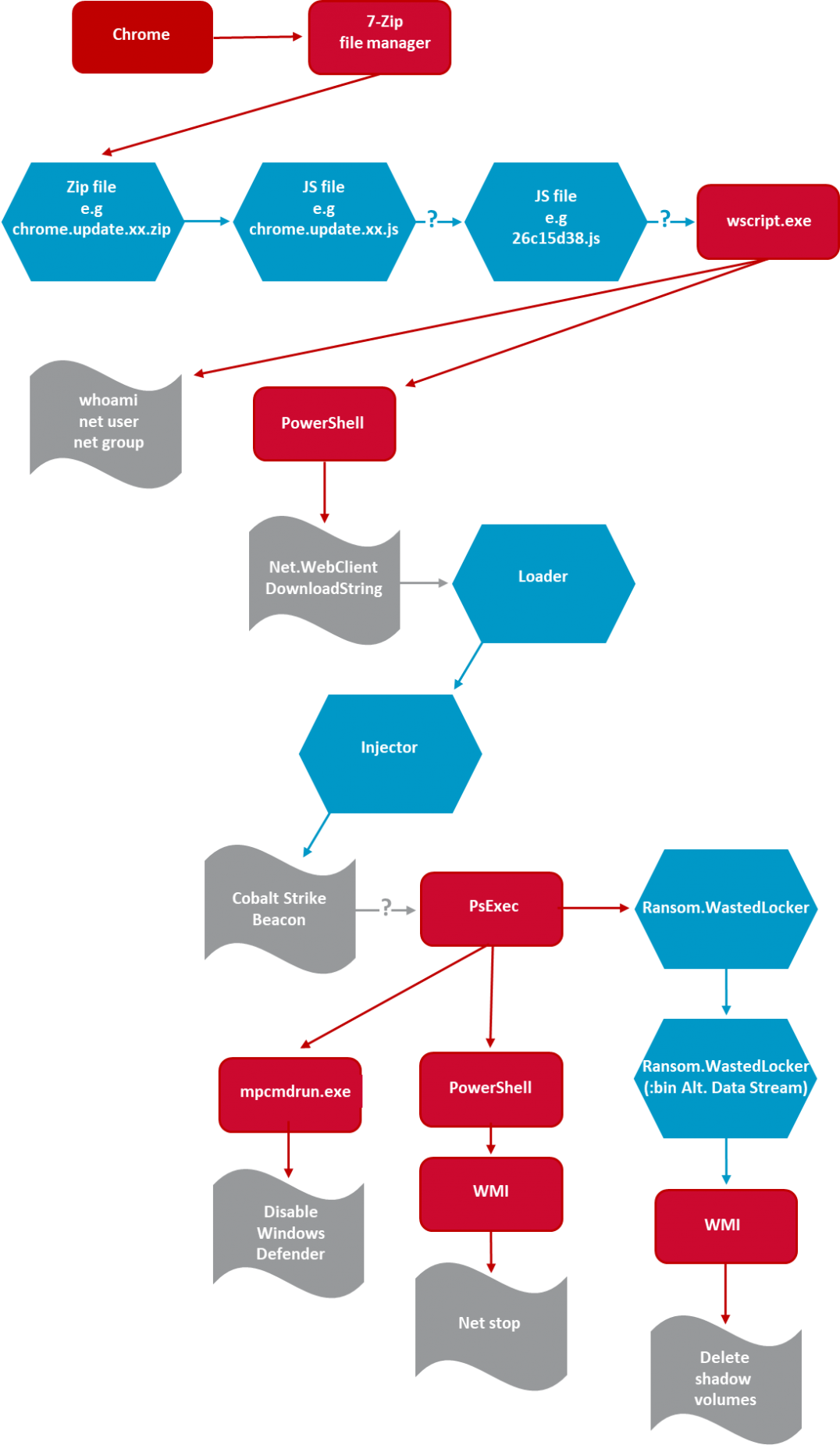
The infection mechanism starts with a malicious JavaScript-based framework known as “SocGholish” delivered in a zipped file to the victim while visiting a compromised legitimate website. As reported, at least 150 compromised websites have been discovered. The zipped file contains malicious JavaScript, masquerading as browser update. Another JavaScript profiles the computer using various commands like whoami, net user, and net group and PowerShell is used to download additional scripts.
The next pivotal stage in this attack is to download and execute a loader from a domain being used to deliver Cobalt Strike threat emulation software. The loader also contains .NET injector. The injected payload, known as Cobalt Strike Beacon, can be used to inject other processes and along with several other tools it can steal credentials, escalate privileges, and move across the network. Attackers also search all computer objects in Active Directory database to locate Windows servers and hosts. Cobalt Strike is also used for credential dumping using “ProcDump”.
Before deploying ransomware, attackers disable Windows Defender across victim’s entire network using PowerShell scripts and legitimate tools. When all the payloads are deployed successfully, Windows Defender is disabled and services across the organization are stopped, Windows Sysinternals tool “PsExec” is used to launch WastedLocker ransomware itself that encrypts the victim’s data and deletes Windows shadow volumes to wipe backups and file snapshots to make recovery impossible.
In the recent attack as analyzed, the malware employs a command line interface to manage its flow of operations. It uses its arguments to encrypt specified directory or files on specified network resource, manipulates its services. Also it manipulates itself to launch from alternate NTFS stream with escalated administrative privilege to bybass UAC prompt to elevate integrity level.
For encrypting files, the operators of Trojan utilizes the combination of AES and RSA algorithms. It generates a unique 256 bit key and a 128 bit IV for encryption of each processed file using the AES-256 algorithm in CBC mode. The AES key, IV and the MD5 hash of the original content, as well as some auxiliary information, are encrypted with a public RSA key (4096 bit) embedded in the trojan’s body. The encryption result (base64 encoded) is saved in new file. Also for each encrypted file a new info file is created.
The threat actors behind this attack are highly experienced and this attack on victim’s network if unidentified and not addressed, can cause substantial damage.
IOC:
IP Address:
- 185.189.151.38
- 185.162.235.167
- 185.82.127.38
- 195.123.227.225
- 38.135.104.189
- 88.119.175.104
- 91.219.237.36
- 91.236.116.63
Domain:
- sodality[d0t]mandmsolicitorscom
- advokat-hodonin[d0t]info/gate[d0t]php
- penaz[d0t]info/gate[d0t]php
- lgrarcosbann[d0t]club/index[d0t]php
- cofeedback[d0t]com
- consultane[d0t]com
- feedbackgive[d0t]com
- msoftwares[d0t]info
- mwebsoft[d0t]com
- net-giftshop[d0t]info
- rostraffic[d0t]com
- traffichi[d0t]com
- typiconsult[d0t]com
- websitesbuilder[d0t]info
- backup[d0t]awarfaregaming[d0t]com
- click[d0t]clickanalytics208[d0t]com
- connect[d0t]clevelandskin[d0t]com
- connect[d0t]clevelandskin[d0t]net
- connect[d0t]clevelandskin[d0t]org
- cushion[d0t]aiimss[d0t]com
- link[d0t]easycounter210[d0t]com
- rocket2[d0t]new10k[d0t]com
- track[d0t]positiverefreshment[d0t]org
Hashes:
- 2cc4534b0dd0e1c8d5b89644274a10c1
- Kindly visit the URL::
https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/wastedlocker-ransomware-us
Countermeasures and Best practices for prevention:
- Maintain appropriate Firewall policies to block malicious traffic entering the system/network. Enable a personal firewall on workstation.
- Keep updated Antivirus/Antimalware software to detect any threat before it infects the system/network. Always scan the external drives/removable devices before use. Leverage anti-phishing solutions that help protect credentials and against malicious file downloads.
- It is also important to keep web filtering tools updated.
- Block the IP addresses of known malicious sites to prevent devices from being able to access them. Activate intelligent website blacklisting to block known bad websites.
- Use limited privilege user on the computer or allow administrative access to systems with special administrative accounts for administrators.
- Block websites hosting JavaScript miners both at the gateway and the endpoints.
- Keep software and OS up-to-date so that attackers may not take advantages of or exploit known vulnerabilities.
- Change default login credentials as they are readily available with attackers.
- Avoid downloading files from untrusted websites.
- Go beyond intrusion detection to protect servers with runtime memory protection
- for critical applications and server workloads, ensuring a defense against actors who already have a grip on your server.
- Disable Autorun and Autoplay policies.
- Consider using application whitelists to prevent unknown executables from launching autonomously.
- Delete the system changes made by the malware such as files created/ registry entries /services etc.
- Monitor traffic generated from client machines to the domains and IP address mentioned in Installation section.
- Disable unnecessary services on agency workstations and servers.
References:
- https://symantec-enterprise-blogs.security.com/blogs/threat-intelligence/wastedlocker-ransomware-us
- https://www.bleepingcomputer.com/news/security/dozens-of-us-news-sites-hacked-in-wastedlocker-ransomware-attacks/
- https://research.nccgroup.com/2020/06/23/wastedlocker-a-new-ransomware-variant-developed-by-the-evil-corp-group/
- https://securelist.com/wastedlocker-technical-analysis/97944/


