Vidar (info-stealing malware)
Original Issue Date:-
January 13, 2023
Virus Type:- info-stealing malware
Severity:-
Medium
It is reported that a new malware campaign, spreading “Vidar” info-stealing malware through spoofing of AnyDesk site is active. More than 1300 domains, impersonating the genuine AnyDesk site, are involved in malicious campaign and redirect to Dropbox folder pushing Vidar and infect endpoints. Since AnyDesk is a popular remote desktop application, it is often abused by malicious actors.
Infection Mechanism:
The hostnames involved in this campaign resolve to the same IP 185[.]149[.]120[.]9. Threat actor utilizes typo squatting to spoof the popular software sites. The list of hostname contains typo squats for AnyDesk, MSI Afterburner, 7-ZIP, Blender, Dashlane, OBS, Slack, VLC, cryptocurrency trading apps, and other prominent softwares. The list of hostnames can be seen through the URL given in IoC section below. Irrespective of name, all the hostnames lead to same AnyDesk clone site, as shown below:
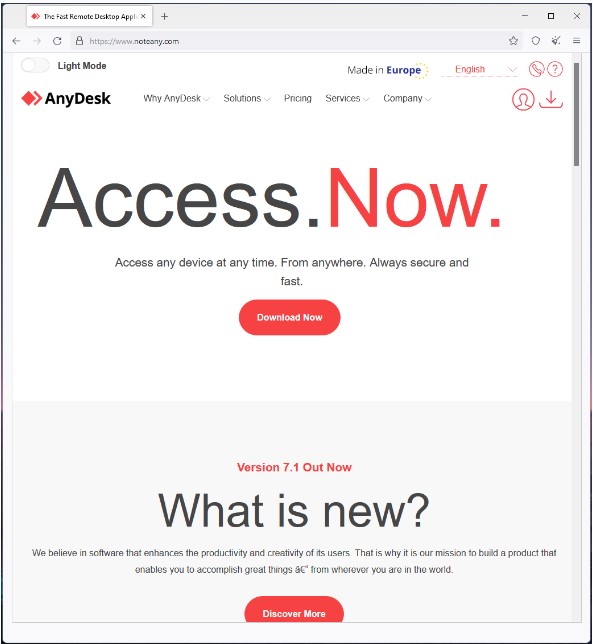
Some of the domains are taken down or blocked by AVs and Dropbox links are also non-functional after the malicious file is reported to cloud storage service. Although, this may be bypassed by threat actor through updating download URL to another site. The impersonating sites are distributing a ZIP file named 'AnyDeskDownload.zip' which is fake installer for AnyDesk. After clicking, it downloads the Vidar information stealing malware.
After infection, the malware search and steals for sensitive information such as account credentials, browser history, saved passwords and cryptocurrency wallet data etc. The data then siphons to the attacker that may further be utilized for malicious activity.
Indicator of Compromise:
IP:
185[.]149[.]120[.]9
Malicious Hostname:
The complete list of hostnames is available here:
https://gist.githubusercontent.com/qbourgue/a81873df59004858a107a7c10b3a3fd7/raw/e731b15ee245bca08834c6da9a69fe8dd16f5f83/vidar_fqdn_impersonating_anydesk_website.txt
Best Practices and Recommendations:
- Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
- Users are advised to update their devices with patches as & when released by respective OEM.
- If devices found infected, it is recommended to re-install the browsers.
- Be aware of the risks of downloading and installing software from untrusted sources and clicking ads or links on suspicious websites.
- Monitor system/ VM resources activity for any abnormal high usage.
- Use a host-based firewall to only allow connections to administrative shares via server message block (SMB) from a limited set of administrator machines.
- Download the softwares from their official OEM website.
- Disable remote Desktop Connections, employ least-privileged accounts. Limit users who can log in using Remote Desktop, set an account lockout policy. Ensure proper RDP logging and configuration.
- Keep the operating system, third party applications (MS office, browsers, browser Plugins) up-to-date with the latest patches.
- Avoid clicking on prompted ads on web pages.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser.
- Users are advised to enable URL filtering solutions on browsers to prevent such attacks.
- Users are advised to use “Browser JSGuard” to detect and defend malicious HTML & JavaScript attacks through web browser based on Heuristics.
Download Link:
For Firefox Web Browser:
https://addons.mozilla.org/en-US/firefox/addon/browser-jsguard/
For Google Chrome Web Browser:
https://chrome.google.com/webstore/detail/browserjsguard/ncpkigeklafkopcelcegambndlhkcbhb
- Additional Security measures that may be considered are:
- Use RDP Gateways for better management
- Change the listening port for Remote Desktop
- Tunnel Remote Desktop connections through IPSec or SSH
- Two-factor authentication may also be considered for highly critical systems
References:


