Tycoon Ransomware
Original Issue Date:- June 27, 2020
Virus Type:- Ransomware
Severity:- Medium
It has been reported that a new ransomware, dubbed “Tycoon” targeting Windows and Linux OS is spreading. The malware strain is involved in highly targeted attack campaign targeting small and medium sized software and educational industries. As identified, the malware was deployed in a targeted attack against an organization where system administrators had been locked out of their systems following an attack on their domain controller and file servers.
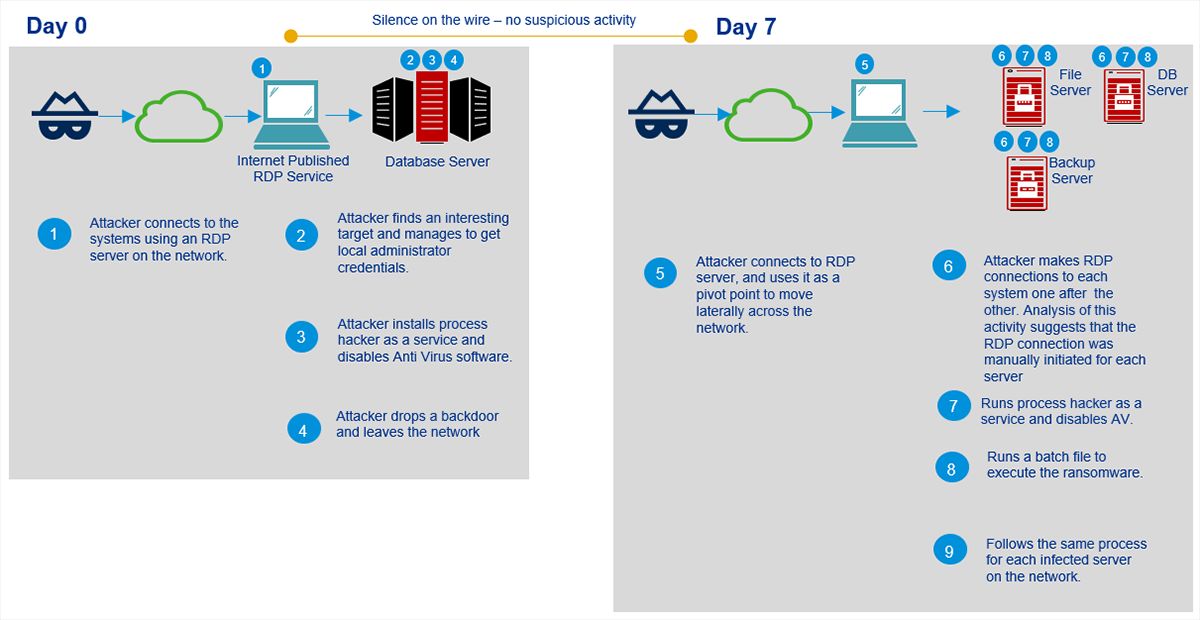
The ransomware, written in Java, is deployed in the form of Trojanized Java Runtime Environment (JRE) build after intruding victim’s network by abusing vulnerable and internet exposed RDP servers. Some peculiar and noteworthy features of this ransomware are:
1. “Image File Execution Options (IFEO) injection” technique is used to gain persistence and execute a backdoor alongside the Microsoft Windows On-Screen Keyboard (OSK) feature of the OS.
2. Anti-malware solutions are disabled using ProcessHacker utility and password of Active Directory servers are changed to deny the access of infected servers.
3. In the final stage, attacker executes Java ransomware module encrypting all file servers including backup systems that are connected to the network.
The malware is compiled into a Java Image file (JIMAGE) located at lib\modules within the build directory. The ransomware uses JIMAGE format to create custom malicious JRE builds executed with the help of shell scripts. Since this malicious JRE build contains both a Windows batch file and a Linux shell, it is presumed that it can encrypt Linux servers as well.
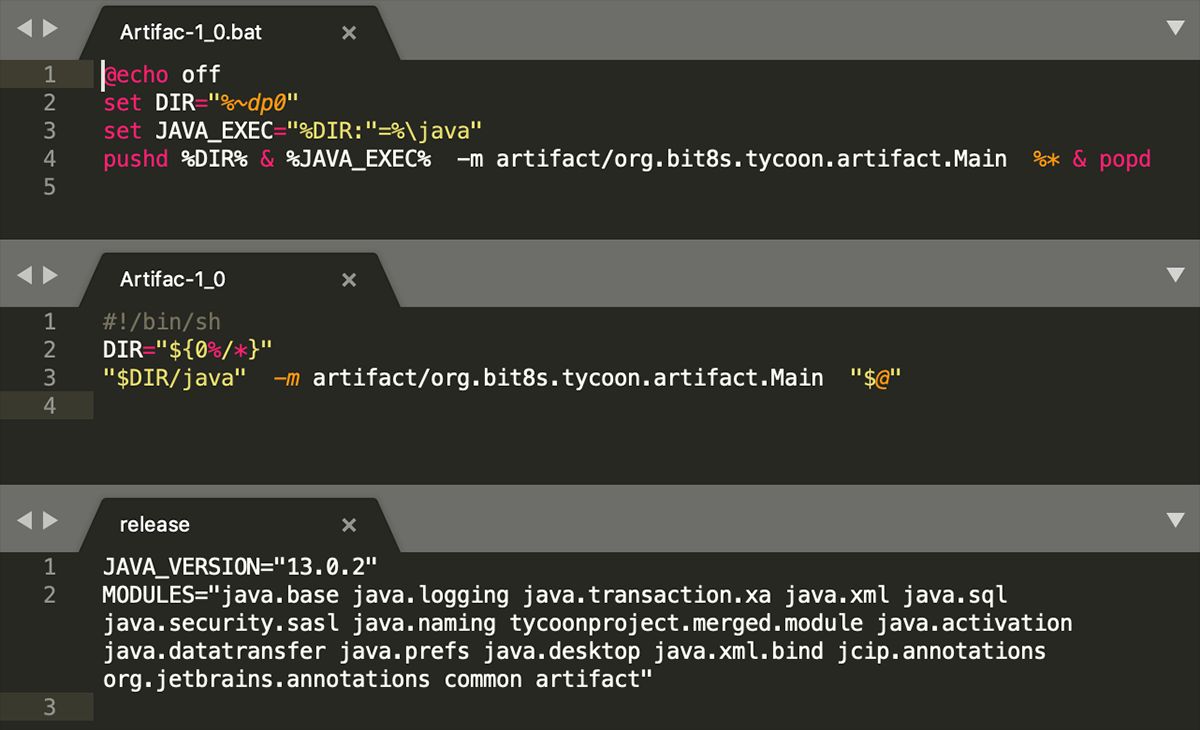
The malware configuration is stored in the project’s “BuildConfig” file and includes various information such as attackers email address, content of ransom note, RSA public key etc.
An install_id value is generated for each victim using the first four bytes from a SHA256 hash of the system UUID value. After encryption process is completed, the malware overwrites deleted files in each encryption path making them irrecoverable.
File Encryption:
The files are encrypted using an AES-256 algorithm in Galois/Counter (GCM) mode [3] with a 16-byte long GCM authentication tag, which ensures data integrity. The encryption chunk size is specified in in BuildConfig and is set to 10MB.For each encryption path, an array of AES-256 keys is generated. Each file (or file chunk, in case of files bigger than the chunk size) is encrypted with a different AES key, then encrypted with the attacker’s RSA-1024 public key and saved in the chunk metadata block. Since asymmetric RSA algorithm is used to encrypt securely generated AES keys, attacker’s private RSA keys are required for decryption. Factoring a 1024-bit RSA key is a herculean task and not realized yet.
While there are some success in decrypting files encrypted by Tycoon with the .redrum extension using a private RSA key obtained from a decryptor bought by one of the victims but files locked by newer versions of Tycoon that use the .grinch and .thanos extensions is not yet possible.
The malware has been active for the last six months at least but the limited no. of victims indicates that this is highly targeted campaign. The overlap in some of the email addresses, the text of the ransom note and the naming convention used for encrypted files, hints a connection between Tycoon and Dharma/CrySIS ransomware.
IOC:
JIMAGE module (lib\modules):
- eddc43ee369594ac8b0a8a0eab6960dba8d58c0b499a51a717667f05572617fb
Email Addresses:
- pay4dec[at]cock[.]lu
- dataissafe[at]protonmail[.]com
- dataissafe[at]mail[.]com
- foxbit[at]tutanota[.]com
- moncler[at]tutamail[.]com
- moncler[at]cock[.]li
- relaxmate[at]protonmail[.]com
- crocodelux[at]mail[.]ru
- savecopy[at]cock[.]li
- bazooka[at]cock[.]li
- funtik[at]tutamail[.]com
- proff-mariarti[at]protonmail[.]com
Encrypted Files Extension:
- thanos
- grinch
- redrum
Encrypted Files Signature:
- happyny3.1
- redrum3_0
RSA Public Key (happyny3.1 version):
Kindly refer the URL:
https://blogs.blackberry.com/en/2020/06/threat-spotlight-tycoon-ransomware-targets-education-and-software-sectors
Countermeasures and Best practices for prevention:
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html - Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
References:


