Triton Malware
Original Issue Date:-
November 13, 2018
Virus Type:-
Trojan
Severity:-
Medium
There are reports of spreading a malware named as Triton which target the industrial safety systems (i.e. Triconex safety controller) of the industry. Industrial safety system (ICS) are used in hazardous plants such as oil, gas and nuclear plants to protect human and plant from environment process which is going beyond the allowed control margins. The mode of spreading this malware is spear phishing mail. The malware allowed the attackers to easily communicate with safety controllers and remotely manipulate system memory to inject shell codes.
Malicious Activity:
- Once attacker reaching the victim network, this malware has capability to laterally move in the network to reach the ICS network of the victim network.
- After reaching the ICS Network of victim, attacker try to communicate with SIS controller deployed in victim network through TriStation communication protocol on port UDP/1502 as shown in Figure1.
- Once it succeed in communicating with SIS controller, malware start reconnaissance the system through requesting the Get Control Program Status and based upon that it start performing malicious activities based upon that response.
- The malware Triton has three main modules: First is injector used for injecting the second module named backdoor which can read, write, and execute access on the Triconex products. The last one is payload which is used by attacker for physical impacting the Devices of the victim.
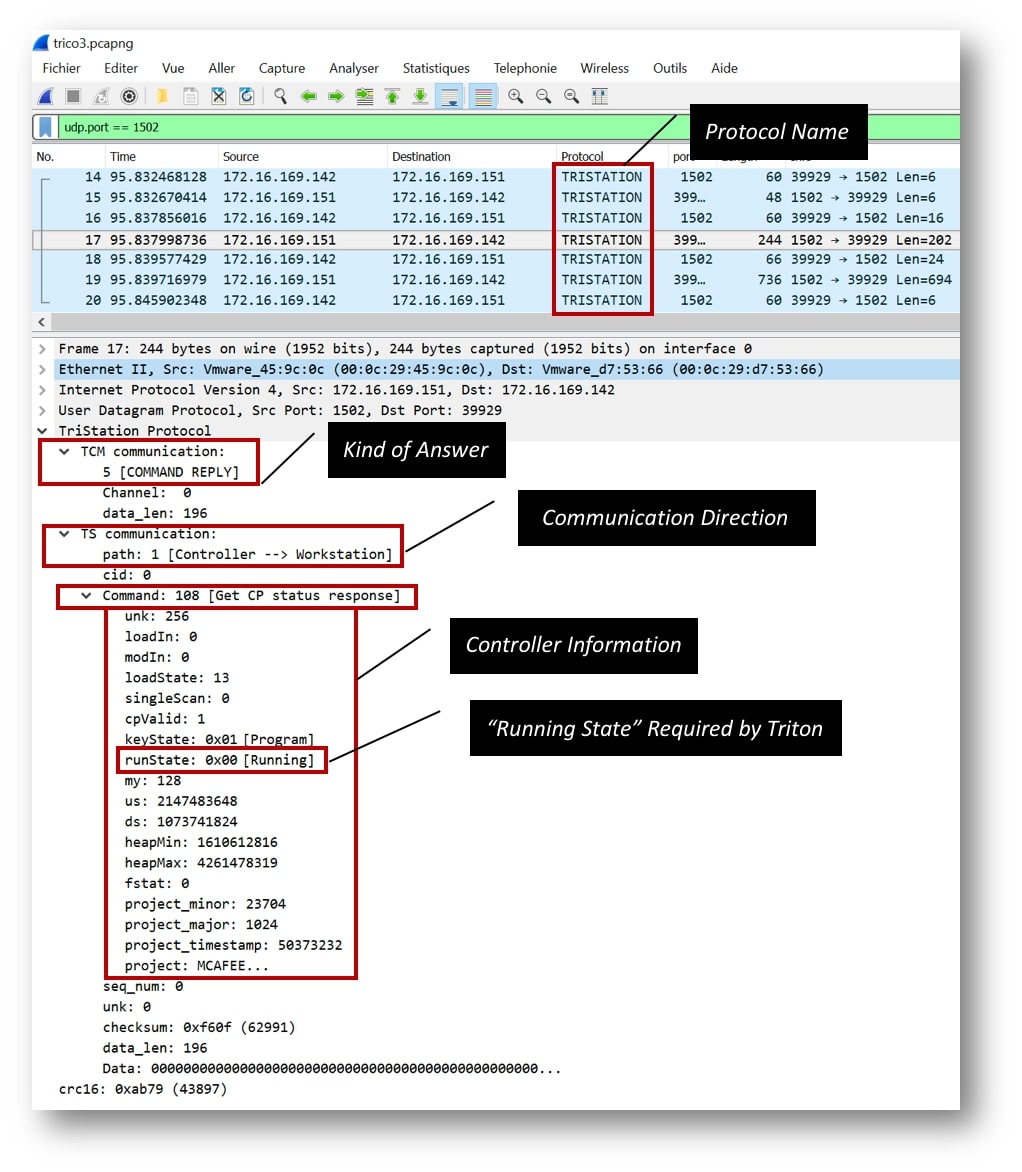
Figure 1. Triconex safety controller communication with malware (Source : securing tomorrow)
Indicators of Compromise:
- dc81f383624955e0c0441734f9f1dabfe03f373c: trilog.exe
- b47ad4840089247b058121e95732beb82e6311d0: imain.bin
- f403292f6cb315c84f84f6c51490e2e8cd03c686: inject.bin
- 91bad86388c68f34d9a2db644f7a1e6ffd58a449: script_test.py
- 1dd89871c4f8eca7a42642bf4c5ec2aa7688fd5c: library.zip
- 97e785e92b416638c3a584ffbfce9f8f0434a5fd: TS_cnames.pyc
- d6e997a4b6a54d1aeedb646731f3b0893aee4b82: TsBase.pyc
- 66d39af5d61507cf7ea29e4b213f8d7dc9598bed: TsHi.pyc
- a6357a8792e68b05690a9736bc3051cba4b43227: TsLow.pyc
- 2262362200aa28b0eead1348cb6fda3b6c83ae01: crc.pyc
- 9059bba0d640e7eeeb34099711ff960e8fbae655: repr.pyc
- 6c09fec42e77054ee558ec352a7cd7bd5c5ba1b0: select.pyc
- 25dd6785b941ffe6085dd5b4dbded37e1077e222: sh.pyc
Best Practices and Recommendations:
- As this malware targets the Triconex MP3008 Firmware v10.0-10.4 MPC860 PowerPC Processor, users are advised to update their firmware once latest one or patch is available for that.
- Users can properly segregate the physical and logical access to ICS networks by using DMZ and firewall so that unauthorized access can be prohibited.
- Properly Logging and monitor every action on the ICS network to quickly identify any suspected traffic.
- Implement proper redundancy on critical devices to avoid major issues.
References:


