SpyMax Android Malware
Original Issue Date:-
June 25, 2025
Virus Type:- Android Remote Access Trojan
Severity:-
Medium
It is reported that a variant of an Android-based Remote Access Trojan (RAT) named SpyMax is currently being distributed via social engineering campaigns. Cybercriminals are targeting mobile users by spreading a fake messaging app such as Telegram or fake wedding invitation app through messaging platforms like WhatsApp. The malware disguises itself as a legitimate app to lure users into granting dangerous permissions, allowing attackers to gain full control over infected devices. Once installed, it steals sensitive user data such as contacts, SMS messages, bank OTPs, and notification content which it sends to an attacker-controlled server.
Infection Mechanism :
As observed, the malware is being distributed through fake wedding invitation app (Wedding Invitation[.]apk) and users are tricked to download the fake apk file.
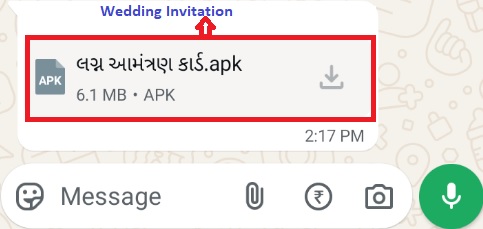
In another latest campaign, the malware is also being distributed through phishing link claiming to be Telegram. When users attempt to download the file, they are redirected to https://telegroms[.]icu/assets/download/ready[.]apk, where a malicious application named ready[.]apk is downloaded.

The victim is enticed to install the file under the pretence of viewing a wedding invitation. Upon installation, the app requests several high-risk permissions including accessibility service, notification access, SMS, permission to install package and to Set as Home App (for persistence). Later, the app icon disappears from the launcher, making it difficult for users to detect or uninstall it. It also decrypts and installs another malicious payload with the package name “com.android[.]pictach”, further expanding its capabilities.
The malware then logs user activity and device information in hidden directories such as: "/Config/sys/apps/log/log-yyyy-mm-dd.log". Captured data including keystrokes, contact lists, SMS content, and notifications is compressed using GZIP and exfiltrated to a Command-and-Control (C2) server at Port 7860.
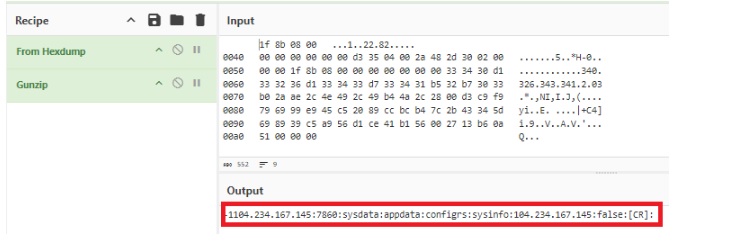
Additionally, SpyMax receives encrypted commands from the server to perform further operations, such as deploying additional payloads or exfiltrating files.
Indicator of Compromise:
C2 IP:
- 104.234.167[.]145
- 154.213.65[.]28:7771
URL:
- https://telegroms[.]icu/assets/download/ready.apk
Package and Hash:
- com.cristal.bristral.tristal[.]mistral - c58b2bacd7c34ef998497032448e3095
- com.android[.]pictach - 66a7fd9bd39b1ba0c097698b68fd94a7
- reputation.printer[.]garmin - 9C42A99693A2D68D7A19D7F090BD2977
Best Practices and Recommendations:
- All users should avoid downloading APKs from outside Google Play and be cautious with risky permission requests while installing any app.
- Reduce the risk of downloading potentially harmful apps by limiting your download sources to official app stores, such as your device’s manufacturer or operating system app store.
- Prior to downloading / installing apps on android devices (even from Google Play Store):
- Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- Do not check "Untrusted Sources" checkbox to install side loaded apps.
- Install Android updates and patches as and when available from Android device vendors.
- Google Play Protect should be enabled on Android device.
- Permissions should also be given carefully.
- Never enable Accessibility Services for unknown or unverified apps.
- Do not browse un-trusted websites or follow un-trusted links and exercise caution while clicking on the link provided in any unsolicited emails and SMSs.
- Install and maintain updated anti-virus and antispyware software.
- Do extensive research before clicking on link provided in the message. There are many websites that allow anyone to run search based on a phone number and see any relatable information about whether or not a number is legit.
- Only click on URLs that clearly indicate the website domain. When in doubt, users can search for the organisation's website directly using search engines to ensure that the websites they visited are legitimate.
- Consider using Safe Browsing tools, filtering tools (antivirus and content-based filtering) in your antivirus, firewall, and filtering services.
- Exercise caution towards shortened URLs, such as those involving bit.ly and tinyurl. Users are advised to hover their cursors over the shortened URLs (if possible) to see the full website domain which they are visiting or use a URL checker that will allow the user to enter a short URL and view the full URL. Users can also use the shortening service preview feature to see a preview of the full URL.
- Look out for valid encryption certificates by checking for the green lock in the browser's address bar, before providing any sensitive information such as personal particulars or account login details.
- Customer should report any unusual activity in their account immediately to the respective bank with the relevant details for taking further appropriate actions.
References:


