Snatch Ransomware
Original Issue Date:- June 27, 2020
Virus Type:- Ransomware
Severity:- Medium
It has been reported that a ransomware dubbed as “Snatch” is on rise and intruding into target organisation’s networks via brute forcing Remote Desktop Protocol (RDP) accounts. Threat actors brute forces a Domain Administrator (DA) account via exposed RDP, further leveraging this to run Meterpreter reverse shell and RDP proxy via TOR on a Domain Controller (DC) leading to encrypt all Domain joined systems. Snatch ransomware will force Windows to reboot in Safe Mode (where most of the software and system drivers will not be running) in order to perform the file encryption process.
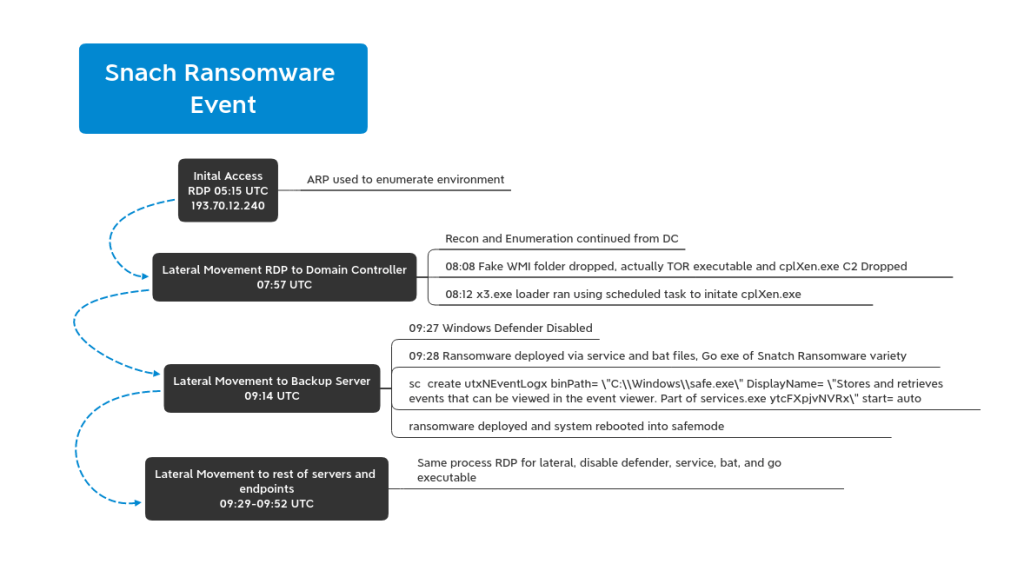
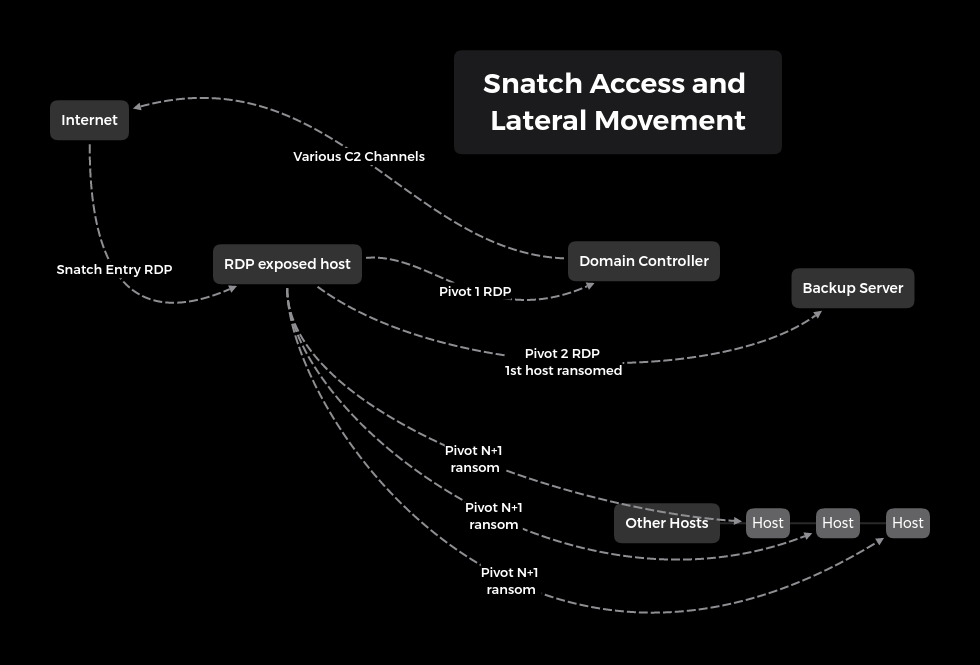
As reported in an attack activity, Snatch team logs into a DA account and perform some basic queries to get further information and then begins lateral movement initiating an RDP session with a DC. Later the attacker deploys a tool set in C:\Windows consisting two executables masqueraded as Windows Management Instrumentation files.
Further a reverse shell is created probably by using Meterpreter. C2 initiated over HTTPS/443 to its IP via cplXen.exe. Another executable serves as loader which in turn persists the loading of cplXen.exe.
After successful connection to C2, “ditsnap” is run on the DC likely to obtain a copy of “ntds.dit” by creating a snapshot. After that attacker accesses RDP into backup server, turns off Windows Defender, and executes safe.exe. This process is done for every machine in the domain followed by all machines ransomed including DC. All machines reboot into safe mode before encrypting causing all logging and remote tools to fail.
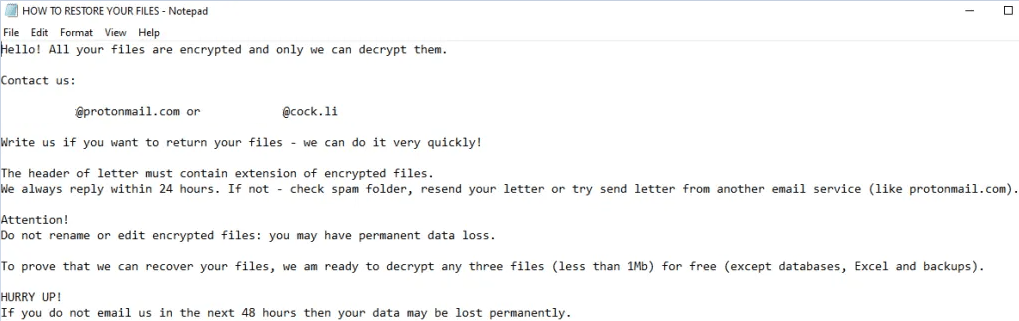
On all machines the following note appears:
IOC:
C2 IP:
- 91.229.77.161
RDP Access IP’s:
- 193.70.12.240
- 178.162.209.135
MD5 Hash:
- 2bbff2111232d73a93cd435300d0a07e
- 1422dae0330c713935d50773680fcb39
- c9a728aa3f5b6f48b68df4bb66b41a5c
- 1f7b17cacb0263b84cf3e9d4a5429ef9
- 6d9d31414ee2c175255b092440377a88
- 3d33a19bb489dd5857b515882b43de12
- 3e36d3dc132e3a076539acc9fcd5535c
- 54fe4d49d7b4471104c897f187e07f91
- 891708936393b69c212b97604a982fed
Countermeasures and Best practices for prevention:
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Deploy Multi factor authentication (MFA) for privileged accounts.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html - Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
References:


