Panchan Botnet
Original Issue Date:-
September 16, 2022
Virus Type:- Botnet / Worm
Severity:-
Medium
It is reported that a new p2p botnet with its main focus on crypto mining through its novel methods, is spreading across the globe. It is dubbed as “Panchan” and currently targeting Linux servers in telecom and education sector organizations. The malware is written in Golang and utilizes concurrency features to enhance spread and execute modules. The botnet/worm take credit of stolen SSH keys for its lateral movement across the network.
Infection Mechanism
As observed, this is a worm that spreads across the network via gaining access through SSH brute force or stealing SSH keys. During brute forcing, it attempts for the credentials with basic user names and passwords. While in the other unique method the malware tries to read ~HOME/.ssh/id_rsa and ~HOME/.ssh/known_hosts files to harvest SSH keys to authenticate credentials for its lateral movement.
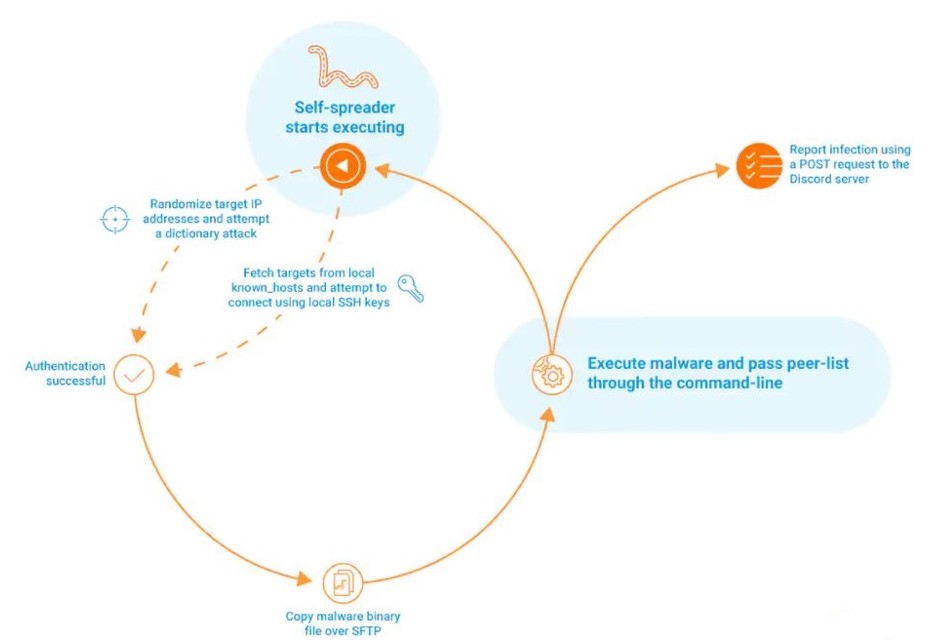
After successfully authentication, the malware creates a hidden folder in root directory and place itself in that folder with the name xinetd using sftp on the target machine. Then the malware binary is remotely executed and supplied with a list of peers. Later, the malware initiates HTTPS POST operation to a Discord webhook. In its peer-2- peer communication, messages are sent as plan text on TCP port 1919, the malware sends configuration commands in specific format.
In its specific feature, the malware itself contains a “godmode”- an admin panel that is capable of customizing the mining configuration and later distributed to peers. To access the godmode admin panel, a private key is required that is verified with the public key contained the malware to open the interface. On the interface, the first section is peer statistics while the second section contains crypto mining configuration that is in same format as mining configuration sent among peers.
The malware deploys two miners- “xmrig” and “nbhash” and their binaries are base64 encoded inside malware itself. The unique feature here is that both the miners are dropped as memory mapped files without any disk presence so it can be executed directly from memory without any traceable path. As observed, the miner use Nicehash for its mining process.
The malware continuously search for process monitoring module (top and htop) and terminates mining if it finds them making it hard to identify.
Indicator of Compromise:
For detailed list of IOC kindly refer the URL:
https://github.com/akamai/akamai-security-research/tree/main/malware/panchan
Best Practices and Recommendations:
- Implement all accounts with complex password logins (e.g., service account, admin accounts, and domain admin accounts) to have strong, unique passwords.
- Implement multi-factor authentication for all services to the extent possible, particularly for webmail, virtual private networks, and accounts that access critical systems.
- Remove unnecessary access to administrative shares.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
- Monitor system/ VM resources activity for any abnormal high usage.
- Use a host-based firewall to only allow connections to administrative shares via server message block (SMB) from a limited set of administrator machines.
- Enable protected files in the Windows Operating System to prevent unauthorized changes to critical files.
- Disable remote Desktop Connections, employ least-privileged accounts. Limit users who can log in using Remote Desktop, set an account lockout policy. Ensure proper RDP logging and configuration.
- Keep the operating system, third party applications (MS office, browsers, browser Plugins) up-to-date with the latest patches.
- Restrict access using firewalls and allow only to selected remote endpoints, VPN may also be used with dedicated pool for RDP access.
- Additional Security measures that may be considered are:
- Use RDP Gateways for better management
- Change the listening port for Remote Desktop
- Tunnel Remote Desktop connections through IPSec or SSH
- Two-factor authentication may also be considered for highly critical systems
References:
- https://www.akamai.com/blog/security/new-p2p-botnet-panchan
- https://www.linode.com/blog/security/linode-security-digest-panchan-malware-lelastic-vulnerability/
- https://thehackernews.com/2022/06/panchan-new-golang-based-peer-to-peer.html
- https://www.techrepublic.com/article/botnet-panchan-attacking-server/


