Mozi IoT Botnet
Original Issue Date:- November 12, 2020
Virus Type:- IoT Botnet
Severity:- Medium
It has been reported that a new malware named Mozi is affecting IoT devices globally. Affected IoT devices are being assembled into an IoT botnet which could be employed by botnet owner for launching distributed denial-of-service (DDoS) attacks, data exfiltration and payload execution.
According to the reports, Mozi malware is comprised of source code from Gafgyt, Mirai, and IoT Reaper; malware families which are targeting IoT devices. Mozi could compromise embedded Linux device with an exposed telnet. It mainly targets home routers and DVRs which are either unpatched, loosely configured or have weak/default telnet credentials. The infected devices form a peer-to-peer (P2P) botnet and uses a distributed hash table (DHT) to communicate with other infected host systems.
The overall network structure is shown in the following figure:
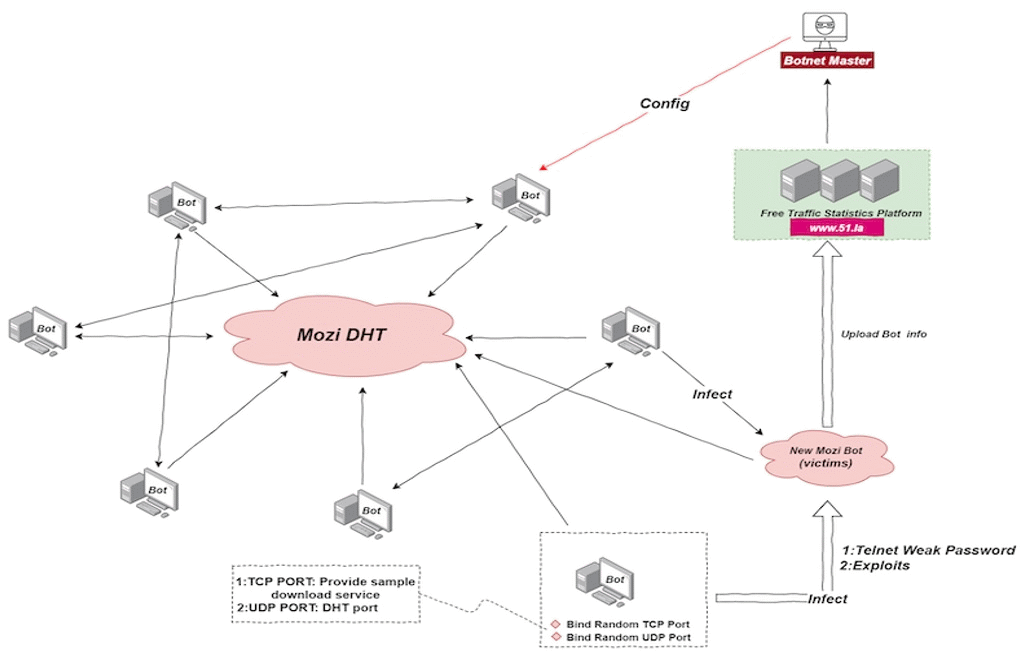
The infection process comprises the follows:
- Current Bot node randomly uses a local port to start the http service to provide sample downloads or receives the sample download address in the Config file issued by the Botnet owner/Master.
- Current Bot node logs in to the target device (which has weak password) and writes the downloader file in echo mode. Later execute it and downloads the sample file from the sample download address provided by the current Bot node. Another way for infecting is by exploiting vulnerability at target, and then obtain a sample file from the sample download address provided by the current Bot node.
- Run the Mozi Bot sample on the infected target device sample file name Mozi.m or Mozi.a join the Mozi P2P network to become the new Mozi Bot node and continue to infect other new devices.
The vulnerabilities exploited by Mozi Botnet are shown as:
| VULNERABILITY | AFFECTED DEVICES |
|---|---|
| Eir D1000 Wireless Router RCI | Eir D1000 Router |
| Vacron NVR RCE | Vacron NVR devices |
| CVE-2014-8361 | Devices using the Realtek SDK |
| Netgear cig-bin Command Injection | Netgear R7000 and R6400 |
| Netgear setup.cgi unauthenticated RCE | DGN1000 Netgear routers |
| JAWS Webserver unauthenticated shell command execution | MVPower DVR |
| CVE-2017-17215 | Huawei Router HG532 |
| HNAP SoapAction-Header Command Execution | D-Link Devices |
| CVE-2018-10561, CVE-2018-10562 | GPON Routers |
| UPnP SOAP TelnetD Command Execution | D-Link Devices |
| CCTV/DVR Remote Code Execution | CCTV DVR |
IOC (Sample MD5):
- eda730498b3d0a97066807a2d98909f3
- 849b165f28ae8b1cebe0c7430f44aff3
IOC (File Hash):
Countermeasures and Best practices for prevention:
Users and administrators are advised to take the following preventive measures to protect their devices:
- Users are advised to update their devices with patches as & when released by respective OEM of devices
- If devices found infected, it is recommended to reset device firmware or restore it from trusted backup.
- Monitor or block UDP traffic from the device to Bit Torrent DHT bootstrap nodes
- Block outgoing TCP traffic with destination ports 22, 23, 2323, 80, 81, 5555, 7574, 8080, 8443, 37215, 49152, and 52869, if not in use.
References:
- https://www.darkreading.com/iot/new-malware-family-assembles-iot-botnet--/d/d-id/1337578
- https://blog.netlab.360.com/mozi-another-botnet-using-dht/
- https://www.internet-sicherheit.de/research/botnetze/iot-botnetze/mozi/
- https://threatpost.com/mozi-botnet-majority-iot-traffic/159337/
- https://securityintelligence.com/posts/botnet-attack-mozi-mozied-into-town/
- https://www.cyberswachhtakendra.gov.in/alerts/mirai.html
- https://www.cyberswachhtakendra.gov.in/alerts/IOT_Botnets_Targeting_Vulnerable_IP_cameras.html
- https://www.cyberswachhtakendra.gov.in/alerts/IOTReaper.html
- https://www.cyberswachhtakendra.gov.in/alerts/BrickerBot_IoT_Malware.html


