Maze ransomware
Original Issue Date:- April 21, 2020
Virus Type:- Ransomware
Severity:- High
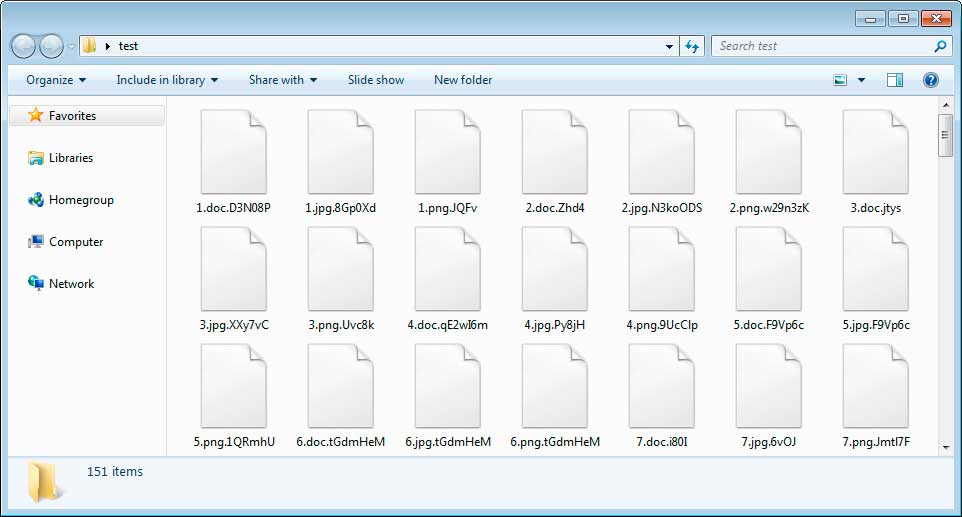
Maze ransomware uses 2048 bit Rivest-Shamir-Adleman (RSA) and ChaCha20 stream cipher encryption to encrypt files. It appends arbitrary extensions to the files during the encryption process. The Maze ransomware executes a “process killer” before starting the encryption processes. Ransomware terminates target processes mainly debuggers, text editors, and programming IDEs, databases and languages running on the infected system. Maze ransomware deletes Shadow Volume Copies twice (pre and post encryption) to ensure that recovery is not possible. It then changes the user's desktop wallpaper to a message about the encrypted files and the file name of the dropped ransom note. The malware tries to make connections to IP addresses that have been crypted in the binary to send information about the infected machine.
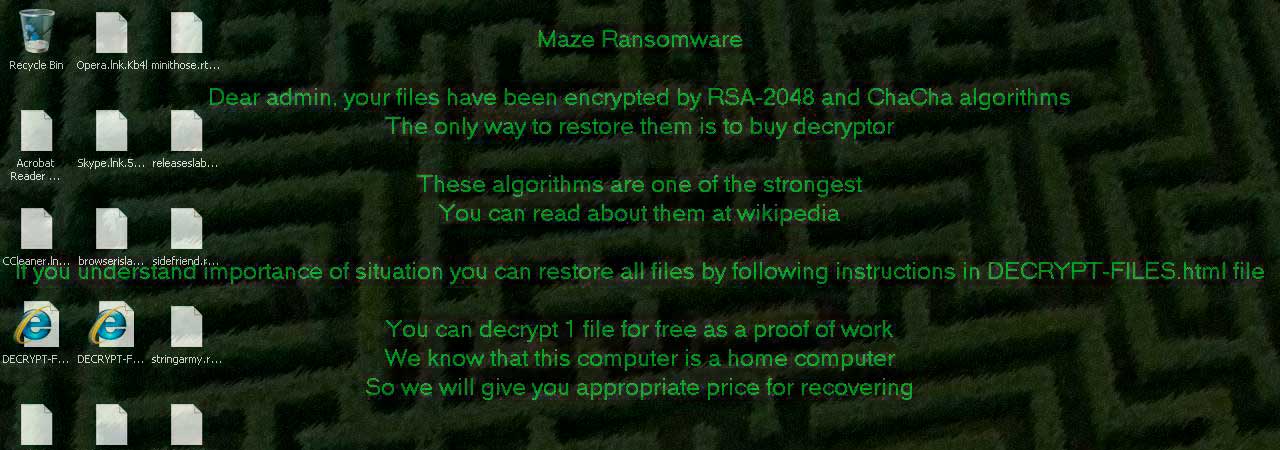
The ransom note asks the victim to contact the threat actor by email for the decryption key. An interesting feature of this ransomware is that it says the ransom amount will be different depending on the type of device. This is uncommon in this ransomware. Maze operators have used the following labels to indicate the user's computer type in the wallpaper message:
- Standalone server
- Server in corporate network
- Workstation in corporate network
- Home computer
- Primary domain controller
- Backup server
- Very valuable for you
Another uncanny characteristic of Maze ransomware has been post compromise cyber extortion in lieu of stolen data. Failing to pay ransom Maze operators release stolen data on the Internet.
Indicators of Compromise:
- SHA256: dee863ffa251717b8e56a96e2f9f0b41b09897d3c7cb2e8159fcb0ac0783611b
- SHA1: 31c3f7b523e1e4060330958e28882227765c3c5e
- SHA256: 6345697c16f84d3775924dc17847fa3ff61579ee793a95248e9c4964da586ddi
- SHA1: c5938ec75e5b655be84eb94d73adecOf63fbce16
- SHA256: 5a900fd26a4ece38de5ca319b5893f96c7e9e2450dbac796c12f85b99238ec18
- SHA1: 1e994b5ac039a1c7612bab93248532bf3ed7e6de
Network IOC’s:
- Mazedecrypt[.]top
- conbase[.]top
- mazedecrypt[.]top
- condurises[.]xyz
- emplementriaton[.]xyz
- fantimit[.]xyz
- 91[.]218.114.11
- 91[.]218.114.25
- 91[.]218.114.26
- 91[.]218.114.31
- 91[.]218.114.32
- 91[.]218.114.37
- 91[.]218.114.38
- 91[.]218.114.4
- 91[.]218.114.77
- 91[.]218.114.79
- 92[.]63.11.151
- 92[.]63.15.6
- 92[.]63.15.8
- 92[.]63.15.56
- 92[.]63.17.245
- 92[.]63.29.137
- 92[.]63.32.2
- 92[.]63.32.55
- 92[.]63.37.100
- 92[.]63.194.3
- 92[.]63.194.20
- 104[.]238.158.250
- 104[.]168.174.32
- 104[.]168.198.208
- 104[.]168.198.230
- 104[.]168.201.35
- 104[.]168.201.47
- 104[.]168.215.54
- 146[.]0.72.85
- 149[.]56.245.196
- 185[.]147.15.22
- 195[.]123.217.13
Associated File Names:
DECRYPT-FILES.%ProgramData%\foo.dat
Countermeasures and Best practices for prevention:
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Security researchers have seen the Spelevo exploit kit delivering Maze ransomware. Since Spelevo exploits outdated browser plugins, users should frequently update their browsers and plugins with the latest security patch.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
References:
- https://www.mcafee.com/blogs/other-blogs/mcafee-labs/ransomware-maze/
- https://www.bleepingcomputer.com/news/security/maze-ransomware-says-computer-type-determines-ransom-amount/
- https://www.herjavecgroup.com/threat-advisory-maze-ransomware/
- https://www.bleepingcomputer.com/news/security/fbi-warns-of-maze-ransomware-focusing-on-us-companies/


