"MalVirt" malware loader
Original Issue Date:-
February 08, 2023
Virus Type:-
malware loader
Severity:-
High
It is reported that a new malvertising campaign, distributing virtualized .NET malware loader that further deploys info-stealer malware, is currently active. The loader, dubbed as “MalVirt” and is distributing malware of “Formbook” info-stealing family. The campaign utilizes KoiVM virtualization technique to evade detection and analysis. KoiVm is a plugin for .NET virtualization protector which uses obfuscation techniques for program opcode. During execution, KoiVM virtualization framework obfuscate the executables by substituting original code such as NET Common Intermediate Language (CIL) instructions, with virtualized code. It is translated back to original form by VM. This makes the malware detection and analysis difficult. The present implementation of KoiVM virtualization framework identifies 119 constant variables to virtualize code construct for example flag and instruction opcode definitions.
As observed, MalVirt loaders is being distributed through Google ads that appear while searching for “Blender 3D” software.
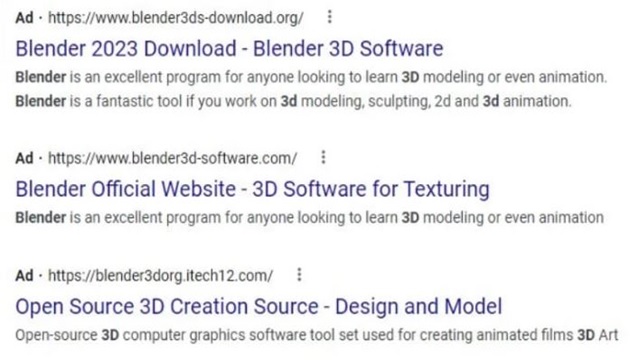
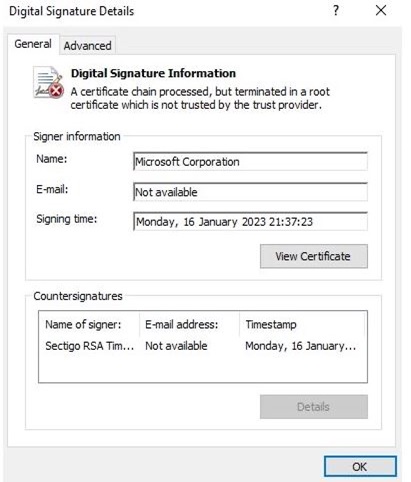
The contents offered by these fake links claim for digital signature which are invalid and impersonating popular provider such as Microsoft, Acer, DigiCert etc.
The loader is equipped with heavy anti-detection and anti-analysis techniques. Further, to bypass static detection, some strings (such as amsi.dll and AmsiScanBuffer) are encoded with Base-64 encoding and AES-encrypted. The loader also has the capability of detecting virtualization environment and if it detects, execution is stopped.
The sample deploy the Process Explorer driver which in turn through kernel privilege kill the processes of detection mechanism and modifying running process to avoid detection.
Moreover, the Formbook itself armed with the capability to disguise its real C2 and IP address. It camouflages its malicious traffic among HTTP requests with encoded and encrypted content to various domains randomly taken from embedded list. Other domains are dummy and act as decoy to confuse analysis. The domains are hosted on various service providers such as Choopa, Namecheap etc.
These evolving attack techniques indicate the attackers’ approach to alternative methods because of default blocking of macros in MS Office.
IoC:
SHA 1:
- 15DB79699DCEF4EB5D731108AAD6F97B2DC0EC9C : MalVirt loader sample
- 655D0B6F6570B5E07834AA2DD8211845B4B59200 : 0onfirm .NET assembly
- BC47E15537FA7C32DFEFD23168D7E1741F8477ED : Process Explorer driver
- 51582417D24EA3FEEBF441B8047E61CBE1BA2BF4 : Infostealer malware payload
Domains:
- www.togsfortoads[.]com : Contacted domain as part of C2 disguise traffic
- www.popimart[.]xyz : Contacted domain as part of C2 disguise traffic
- www.kajainterior[.]com : Contacted domain as part of C2 disguise traffic
- www.heji88.hj-88[.]com : Contacted domain as part of C2 disguise traffic
- www.headzees[.]com : Contacted domain as part of C2 disguise traffic
- www.in-snoqualmievalley[.]com : Contacted domain as part of C2 disguise traffic
- www.365heji[.]com : Contacted domain as part of C2 disguise traffic
- www.h3lpr3[.]store : Contacted domain as part of C2 disguise traffic
- www.graciesvoice[.]info : Contacted domain as part of C2 disguise traffic
- www.femfirst.co[.]uk : Contacted domain as part of C2 disguise traffic
- www.cistonewhobeliev[.]xyz : Contacted domain as part of C2 disguise traffic
- www.allspaceinfo[.]com : Contacted domain as part of C2 disguise traffic
- www.baldur-power[.]com : Contacted domain as part of C2 disguise traffic
- www.ohotechnologies[.]com : Contacted domain as part of C2 disguise traffic
- www.carlosaranguiz[.]dev : Contacted domain as part of C2 disguise traffic
- www.iidethakur[.]xyz : Contacted domain as part of C2 disguise traffic
- www.huifeng-tech[.]com : Contacted domain as part of C2 disguise traffic
Countermeasures:
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only. Users must be aware while clicking on links during web search
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most attacks.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- Prohibit external FTP connections and blacklist downloads of known offensive security tools.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis. https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
References:


