Gandcrab Ransomware
Original Issue Date:-
March 26, 2018
Virus Type:-
Trojan/Ransomware
Severity:-
High
A large scale ransomware campaign dumped
Once the victim computer is infiltrated with Gandcrab ransomware, it queried the victim computer to get information like username, keyboard type, presence of antivirus, IP, OS version, current Windows version etc. Based upon the information it got, Gandcrab decide its further strategy like if some process is running on the victim system, then it first kill that process to unlock the files which are hold by that process so that Gandcrab ransomware can encrypt all the files of the victim computer.
After it, Gandcrab calls the built-in crypto functions to generate the public and private keys on the victim computer and send these keys with the all information (OS version, antivirus name etc.) about the victim computer it got earlier to C2 server which is hosted on .bit domain.
Now Gandcrab starts encrypting all the files (except some files which it considers as protected file) of the victim computer using public key it generate at earlier step and add the ".GDCB" extension (Figure 1) to the name of all encrypted file. After encrypting, Gandcrab generates a "GDCB-DECRYPT.txt" file which contains the message asking for ransom from the victim to decrypt their encrypted data.
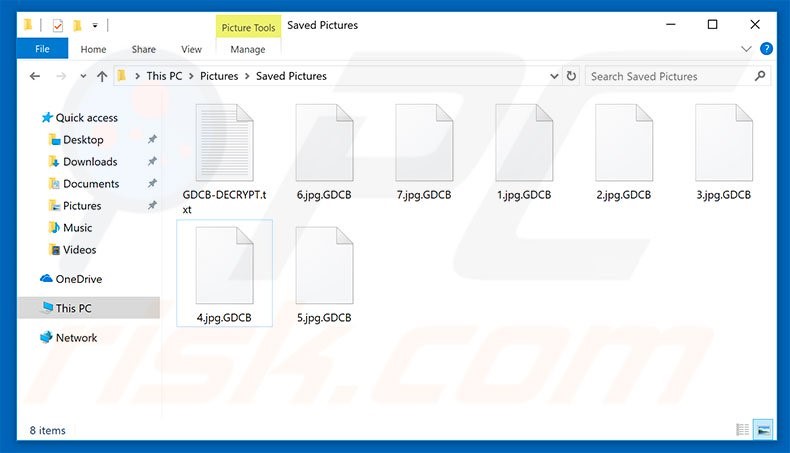
Fig1. Files encrypted with. GDCB Extension (source:pricsk)
Indicators of Compromise:
Seamless gate:
- 31.31.196.187,xn--80abmi5aecft.xn--p1acf
GrandSoft EK (IP):
- 62.109.4.135
- 92.63.197.59
- 66.171.248.178
- 5.104.188.117
- 188.172.82.30
- 66.171.248.178
- 188.172.82.30
- 90.141.200.228
Hashes:
- 69f55139df165bea1fcada0b0174d01240bc40bc21aac4b42992f2e0a0c2ea1d GandCrab (packed)
- ab0819ae61ecbaa87d893aa239dc82d971cfcce2d44b5bebb4c45e66bb32ec51 GandCrab (unpacked)
- 6a19146eb0ae8a352b166454f69bf95b4152f43b9692b4c014f9258f43be8d02(Flash exploit, SWF file)
- 3c60a9af0f5538f3bca64a1df5c604a6d194495d8d5a66bcd1a4f09b84015ebb (EITest campaign payload, Executable file)
- 69f55139df165bea1fcada0b0174d01240bc40bc21aac4b42992f2e0a0c2ea1d (Seamless-campaign Rig EK payload, Executable file)
- 496a5f41e206b552c93690926d6678b2f2550fe14db8dbdc42e6532353735c13(Flash exploit, SWF file)
Countermeasures:
- Perform regular backup of all the critical information to minimize the loss.
- Keep the operating system and third party applications (MS office, browsers, browser Plugins, antivirus) up-to-date with the latest patches.
- Follow safe practices when browsing the web. Ensure the web browsers are secured enough with appropriate content controls.
- Victim can try with online Decryptor available (Bit defender) for Gandcrab ransomware to get back their encrypted data.
References:


