Diavol Ransomware
Original Issue Date:-
December 21, 2021
Virus Type:- Ransomware
Severity:-
Low
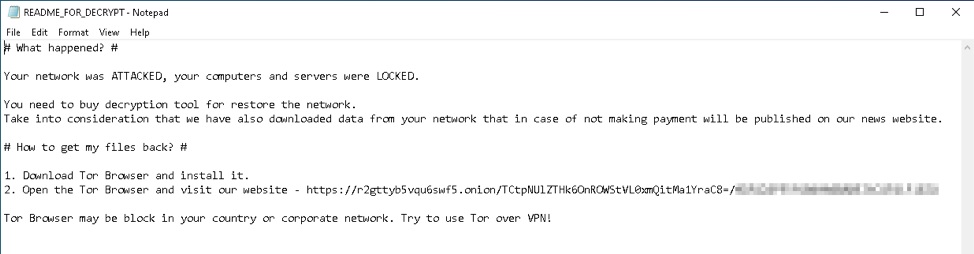
It has been reported that a newly surfaced malware named ‘Diavol Ransomware’ compiled with Microsoft Visual C/C++ Compiler is encrypting files using user-mode Asynchronous Procedure Calls (APCs) with an asymmetric encryption algorithm. Recently, it has been reported that the Diavol malware has been spreading via email, which includes a link to OneDrive. The OneDrive link, directs the user to download a zipped file which included an ISO file containing a LNK file and a DLL. Once opened (mounted) on the users system, the LNK file masqueraded as a Document entices the user to click/open it. Once the user executes the LNK file, the malware infection will be initiated.
Infection Mechanism
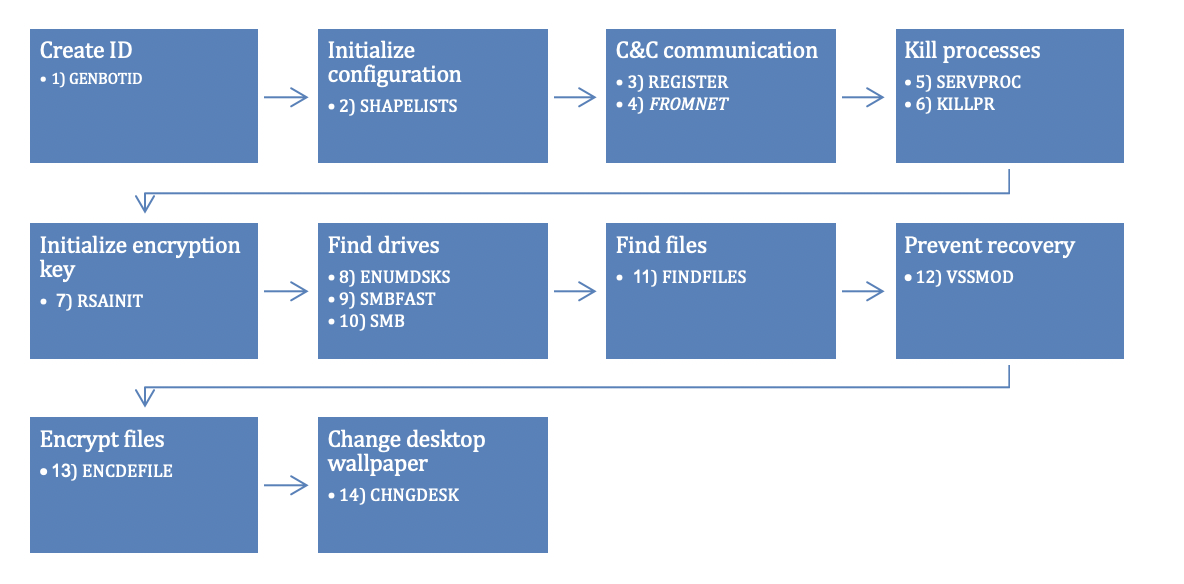
Once executed, the Diavol malware carries out pre-processing on the victim system including registering the victim device with a remote server, terminating running processes, finding local drives and files in the system to encrypt, and preventing recovery by deleting shadow copies. Then, the files are locked and desktop wallpaper is changed with a ransom message.
Diavol also lacks any obfuscation as it doesn't use packing or anti-disassembly tricks, but it still manages to make analysis harder by storing its main routines within bitmap images.
When executing on a compromised machine, the ransomware extracts the code from the images' PE resource section and loads it within a buffer with execution permissions. The ransomware generates a System/Bot ID with the following format:
<hostname>-<username>_W<windows _version>.<guid>
For example:
- DESKTOP-4LUGU5I-reuser_W10019041.C3F3799FE69249579857D2039BBBAB11
This format is almost identical to the Bot ID generated by TrickBot malware, except that the username field has been added.
Ransomware extracts the code amounts to 14 different routines that will execute in the following order:
Indicator of Compromise:
Hashes (SHA 256)
- 85ec7f5ec91adf7c104c7e116511ac5e7945bcf4a8fdecdcc581e97d8525c5ac (locker.exe)
Best Practices and Recommendations to protect users against the threat of ransomware:
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most attacks.
- Scan all incoming and outgoing emails to detect threats and filter executable files from reaching end users.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
- Restrict users’ permissions to install and run software applications, and apply the principle of “least privilege” to all systems and services. Restricting these privileges may prevent malware from running or limit its capability to spread through a network.
- Configure firewalls to block access to known malicious IP addresses.
- Users are advised to disable their RDP if not in use, if required it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Restrict execution of Power shell /WSCRIPT in enterprise environment Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis. https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization's website directly through browser.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf consider encrypting the confidential data as the ransomware generally targets common file types.
- Carry out vulnerability Assessment and Penetration Testing (VAPT) and information security audit of critical networks/systems, especially database servers from CERT-IN empanelled auditors. Repeat audits at regular intervals.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
Generic Prevention Tools:
Sophos: Hitman.Pro https://www.hitmanpro.com/en-us/surfright/alert.aspx
Malwarebytes Anti-Ransomware (formally Crypto Monitor) https://blog.malwarebytes.com/malwarebytes-news/2016/01/introducing-the-malwarebytes-anti-ransomware-beta/
Trendmicro Ransomware Screen Unlocker tool: https://esupport.trendmicro.com/en-us/home/pages/technical-support/1105975.aspx
Trend Micro (Trend-micro-ransomware-file-decryptor) https://success.trendmicro.com/solution/1114221-downloading-and-using-the-trend-micro-ransomware-file-decryptor
References:
- https://thedfirreport.com/2021/12/13/diavol-ransomware/
- https://www.fortinet.com/blog/threat-research/diavol-new-ransomware-used-by-wizard-spider
- https://www.bleepingcomputer.com/news/security/trickbot-cybercrime-group-linked-to-new-diavol-ransomware/
- https://securityintelligence.com/posts/analysis-of-diavol-ransomware-link-trickbot-gang/
- https://www.csk.gov.in/alerts/ransomware.html


