Dark Pulsar
Original Issue Date:-
October 24, 2018
Virus Type:-
Backdoor Malware
Severity:-
Medium
Dark pulsar is a backdoor which got installed on the victim system through the Eternal Blue exploit, a SMBv1 (Server Message Block 1.0) vulnerability present in Microsoft Operating system. Once this malware reach on victim machine, it opens a backdoor through which other plugin of this malware get loaded onto infected computers. These plugin enhance the functionality of attacker like Responds to a specific ping request of C2 controlled by attacker, load shell code, disable security, enabled the security, payload upload, upgrade implant, run a DLL on the victim machine, Process injection, maintaining persistence and uninstall itself.
Once backdoor fully installed on the victim machine, attacker check its presence by sending the "trans2 SESSION_SETUP" request to the victim machine. Based upon the victim machine response, attacker know that it is infected or not. If a system is found to be infected with this backdoor, then attacker used the SMB as a covert channel to exfiltrate data or launch remote command on the victim machine to perform malicious activity. The port used by attacker for Exfiltrate data from victim machine is not new but the same port used for SMB via 445 as shown in Figure1.
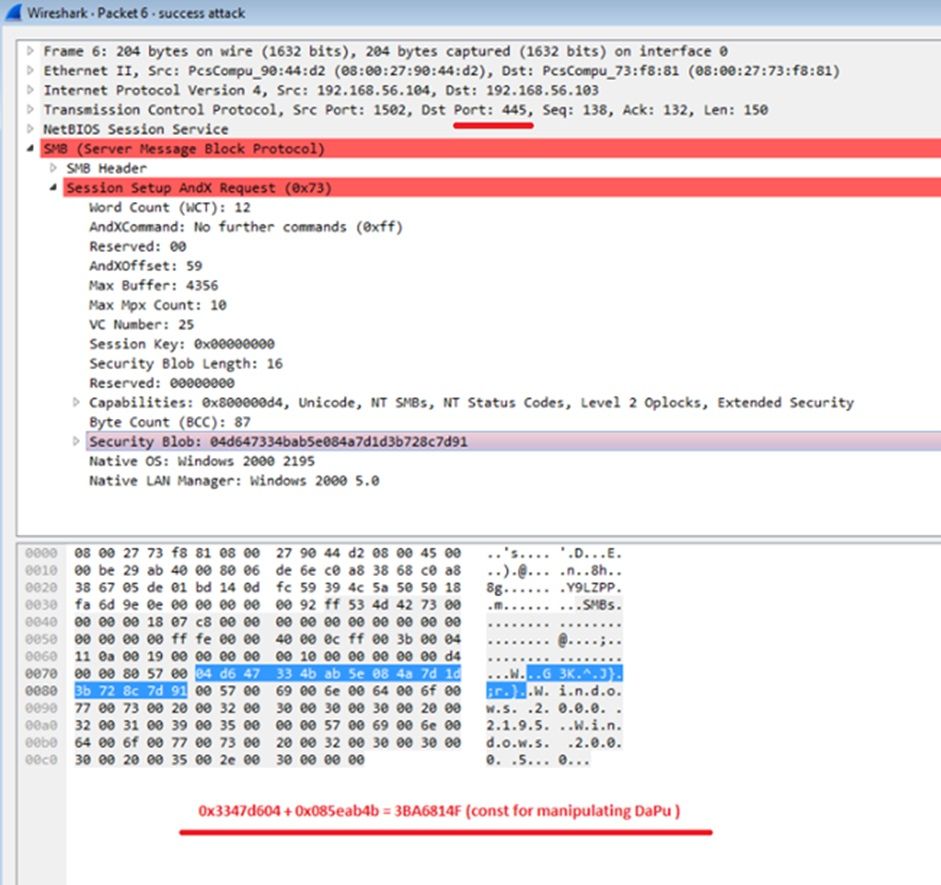
Fig 1. Network traffic on Port no. 445 build by Dark pulsar on victim machine (Source: secure list)
Indicators of Compromise:
MD5:
- 96f10cfa6ba24c9ecd08aa6d37993fe4
File Location:
- %SystemRoot%\System32\sipauth32.tsp
Registry:
- HKLM\Software\Microsoft\Windows\CurrentVersion\Telephony\Providers
Best Practise and Recommendations:
- Users are advised to patch their system from Eternal Blue exploit vulnerability having CVE no.
CVE-2017-0144with latest patch released by Microsoft from below mentioned link.
https://docs.microsoft.com/en-us/security-updates/securitybulletins/2017/ms17 -010
- Blocks users from connecting to malicious domains, IPs, and URL. Monitor all the outward network connection build by your machine with port no 445..
- Restrict execution of PowerShell /WSCRIPT in enterprise environment Ensure installation and use of latest version (currently v5.0) of PowerShell, with enhanced logging enabled. Script block logging, and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
- Follow safe practices when browsing the web.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Generally Malware sample drops and executes generally from these locations.
Reference:https://www .fireeye.com/blog/threatresearch/2016/02/greater_visibilityt.html
References:


