Conti Ransomware
Updated on:- March 10, 2022
Original Issue Date:- July 20, 2020
Virus Type:- Ransomware
Severity:- Medium
It has been reported that a new ransomware, named “Conti ransomware” is spreading. In its infection stages, threat actors breach the corporate networks and spread laterally to acquire domain administration privilege for deploying ransomware. The coding pattern of Conti appears similar to erstwhile “Ryuk ransomware” version 2 and ransomware note used is also same as Ryuk had dropped in its earlier attacks. Moreover, the same TrickBot infrastructure is utilized by both Ryuk and Conti threat actors as part attacking mechanism. Conti is a human-operated ransomware designed to be directly controlled by its operator rather than execute automatically by itself.
Infection mechanism:
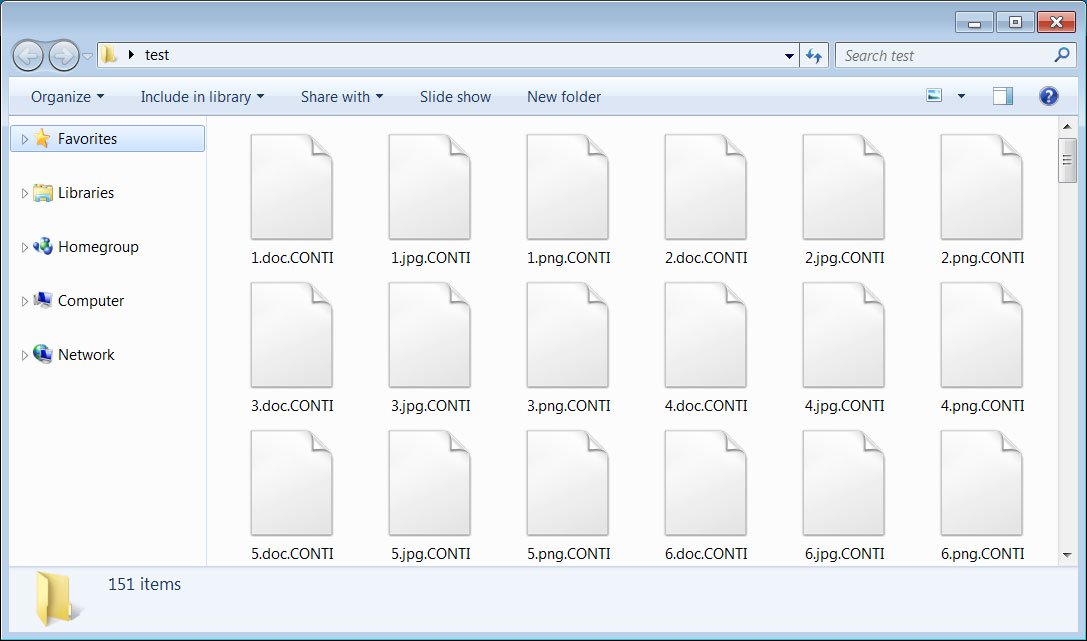
When starts, Conti executes 146 commands focused on stopping potential Windows services related to security, backup, database and email solutions. Then it deletes the Volume Shadow Copies in a unique way and begins encryption. The ransomware appends the .CONTI extension to encrypted files and drop a ransom note named CONTI_README.txt in each folder.
When encrypting data, the ransomware uses a unique AES-256 encryption key per file, which is then encrypted with a bundled RSA-4096 public encryption key (unique per victim).
Conti ransomware is also special in its selection of encryption targets that could be local hard drive or network shares, even specific, targeted, IP addresses via a command-line client. It can be configured to skip encrypting files on local drives and encrypt data on networked SMB shares. This may lead to targeted damage and may cause destruction limited to shares of a server that has no internet capability making it likely unnoticeable for days or weeks.
It also supports an '--encrypt_mode' argument to upgrade its encryption strength. When using '—encrypt_mode local,' only the local drives are encrypted, and when using the '—encrypt_mode network,' only the network shares are encrypted.
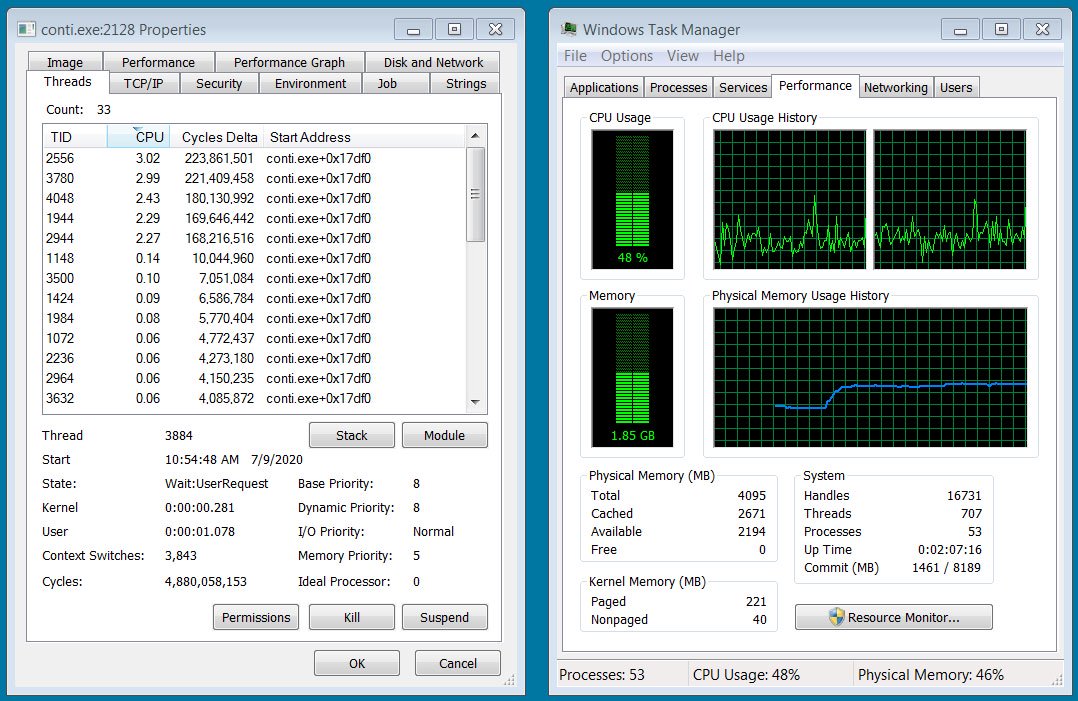
Another notable feature of Conti ransomware is that it utilizes a large no. of concurrent CPU thread, namely 32 threads for encrypting different files simultaneously with a very fast speed. However due to this, CPU and disk utilization goes up causing of machine become sluggish and may serve as an alarming situation for a user.
Another feature observed that its code abusing “Windows Restart Manager” - the Windows component that unlocks files before performing an OS restart. Conti utilizes this component to unlock and shut down app processes so it can encrypt their respective data. This technique can be phenomenal on Windows servers where sensitive data is usually managed by a database and almost always up and running.
IOC:
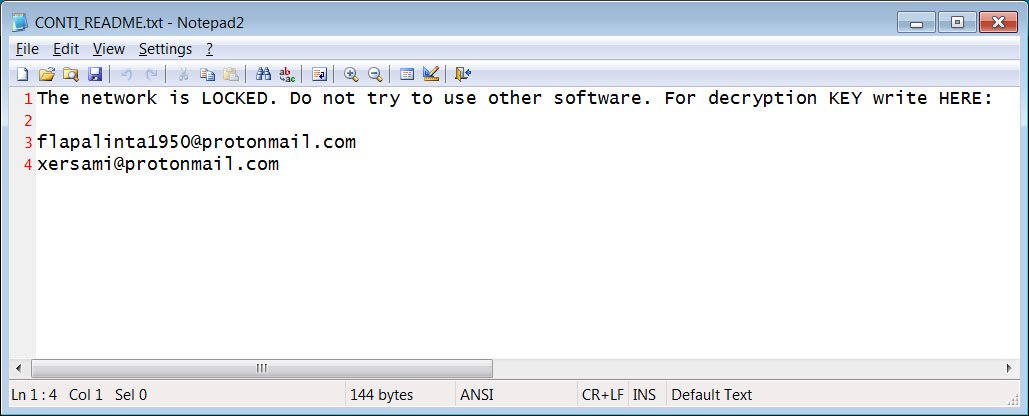
Associated emails:
- flapalinta1950@protonmail[dot]com
- xersami@protonmail[dot]com
For Metadata for the Conti malware sample, AES-256 public key used for encryption and another detailed IOC please refer the URL:
Countermeasures and Best practices for prevention:
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis.
https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html - Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths. Ransomware sample drops and executes generally from these locations.
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
References:
- https://www.cisa.gov/uscert/ncas/alerts/aa21-265a
- https://www.carbonblack.com/blog/tau-threat-discovery-conti-ransomware/
- https://www.bleepingcomputer.com/news/security/conti-ransomware-shows-signs-of-being-ryuks-successor/
- https://www.zdnet.com/article/conti-ransomware-uses-32-simultaneous-cpu-threads-for-blazing-fast-encryption/


