SyncFuture Espionage Targeted Campaign (Blackmoon Malware)
Original Issue Date:-
February 06, 2026
Virus Type:- Backdoor
Severity:-
Medium
It is reported that a targeted cyber-espionage campaign is affecting users and organisations in India. The campaign is assessed to be highly targeted indicating deliberate victim selection and reconnaissance by the threat actors. It primarily leverages social engineering and trusted-looking government communication themes to gain initial access, making it particularly dangerous for unsuspecting users. Successful exploitation of this campaign can result in unauthorized and persistent access to compromised systems, enabling attackers to silently monitor user activity, collect sensitive information and potentially exfiltrate confidential data over extended period.
Infection Mechanism:
The campaign uses phishing emails impersonating the Indian Income Tax Department to deliver a multi-stage malware infection chain. The infection begins with a malicious attachment and ultimately deploys a surveillance framework by abusing legitimate enterprise remote management software (SyncFuture TSM). A key malware component involved in the early stage of this campaign is identified as Blackmoon malware, which acts as a loader and persistence mechanism. Initially, a phishing email delivers a ZIP archive containing a disguised executable. Once executed, Blackmoon malware is launched, which is responsible for initial execution, establishing persistence, downloading additional payloads and enabling installation of the SyncFuture remote access component.
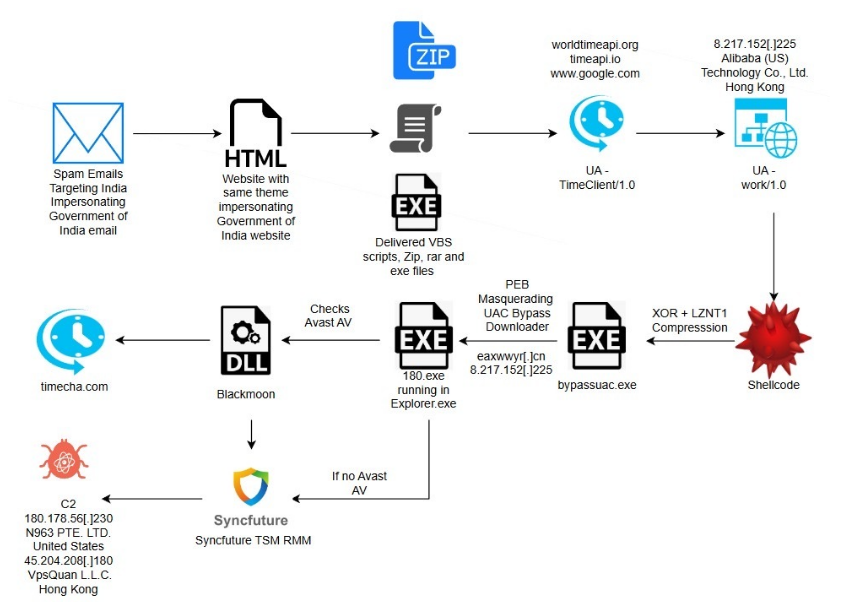
The fraudulent phishing email closely mimics official tax notices, using authoritative language and formatting to pressure recipients into opening the attached ZIP file. The attachment is presented as a legitimate tax-related document, increasing the likelihood of execution.

Because the campaign abuses legitimate and digitally signed remote management software, detection becomes more difficult, increasing the risk to government entities, enterprises and targeted individuals and allowing the threat actors to maintain long-term presence without raising immediate suspicion.
Indicator of Compromise:
For detailed list of IoC, kindly refer the below URL:
Best Practices and Recommendations:
- Don't open attachments in unsolicited e-mails, even if they come from people in your contact list, and never click on a URL contained in an unsolicited e-mail, even if the link seems benign. In cases of genuine URLs close out the e-mail and go to the organization’s website directly through browser.
- Update software and operating systems with the latest patches. Outdated applications and operating systems are the targets of most attacks.
- It is advised to block office applications from creating executable files.
- Install ad blockers to combat exploit kits such as Fallout that are distributed via malicious advertising.
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only. Users must be aware while clicking on links during web search.
- Prohibit external FTP connections and blacklist downloads of known offensive security tools.
- All operating systems and applications should be kept updated on a regular basis. Virtual patching can be considered for protecting legacy systems and networks. This measure hinders cybercriminals from gaining easy access to any system through vulnerabilities in outdated applications and software. Avoid applying updates / patches available in any unofficial channel.
- Restrict execution of Power shell /WSCRIPT in an enterprise environment. Ensure installation and use of the latest version of PowerShell, with enhanced logging enabled. Script block logging and transcription enabled. Send the associated logs to a centralized log repository for monitoring and analysis. https://www.fireeye.com/blog/threat-research/2016/02/greater_visibilityt.html
- Establish a Sender Policy Framework (SPF) for your domain, which is an email validation system designed to prevent spam by detecting email spoofing by which most of the ransomware samples successfully reaches the corporate email boxes.
- Application whitelisting/Strict implementation of Software Restriction Policies (SRP) to block binaries running from %APPDATA% and %TEMP% paths.
- The organization should have a corporate policy for acceptable use of corporate devices which prohibits the use of any unauthorized third-party software.
- Users are advised to disable their RDP if not in use, if required, it should be placed behind the firewall and users are to bind with proper policies while using the RDP.
- Block the attachments of file types, exe|pif|tmp|url|vb|vbe|scr|reg|cer|pst|cmd|com|bat|dll|dat|hlp|hta|js|wsf
- Consider encrypting the confidential data as the ransomware generally targets common file types.
- Perform regular backups of all critical information to limit the impact of data or system loss and to help expedite the recovery process. Ideally, this data should be kept on a separate device, and backups should be stored offline.
- Network segmentation and segregation into security zones - help protect sensitive information and critical services. Separate administrative network from business processes with physical controls and Virtual Local Area Networks.
References:
- https://www.esentire.com/blog/weaponized-in-china-deployed-in-india-the-syncfuture-espionage-targeted-campaign
- https://www.cyfirma.com/research/digital-frontlines-india-under-multi-nation-hacktivist-attack/
- https://www.broadcom.com/support/security-center/protection-bulletin/blackmoon-s-expanding-arsenal
- https://inceptioncyber.ai/blog/geopolitically-motivated-hacktivist-campaigns-recent-coordinated-cyber-attacks-targeting-indian-corporations


