Android: BlackRock Malware
Original Issue Date:- July 27, 2020
Virus Type:- Android Trojan
Severity:- Medium
It is reported that a new Android malware strain, dubbed “BlackRock”, equipped with data stealing capabilities, is attacking a wide range of android applications. The malware is developed using the source code of Xerxes banking malware, which itself is a variant of LokiBot android Trojan.
The noteworthy feature of this malware is that the target list of applications of this malware which contains 337 applications includes not only banking and financial applications but also non-financial well known commonly used brand name apps on android device with a focus on social, communication, networking and dating platforms. It can steal credentials and credit card information from targeted 300+ apps like email clients, e-commerce apps, virtual currency, messaging/social media apps, entertainment apps, banking, financial apps etc. (Kindly refer the first link listed in References below for complete list of apps.) The attack campaign is active globally.
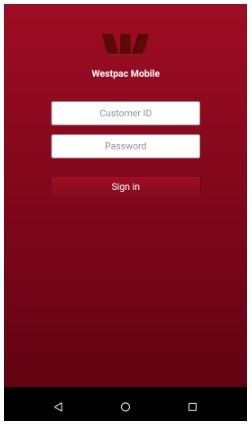
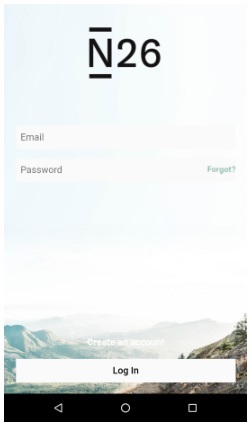
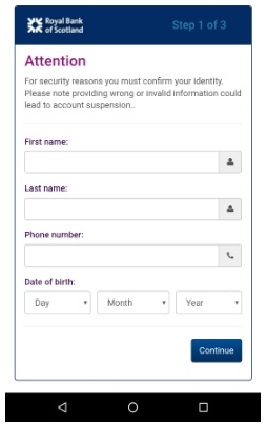
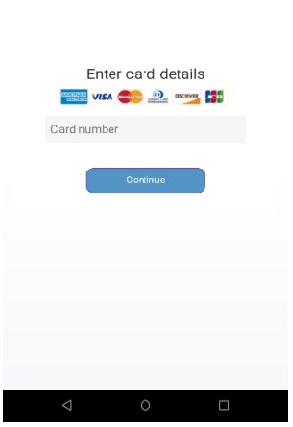
When the malware is launched on the victim’s device, firstly it hides its icon from app drawer and then masquerades itself as a fake Google update to request Accessibility service privileges.
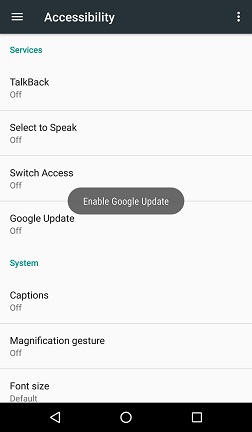
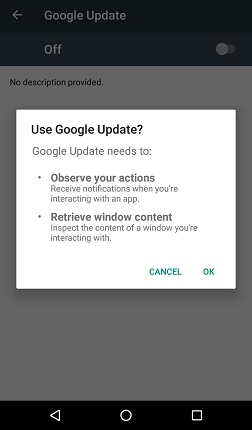
Once this privilege is granted, it becomes free to grant itself additional permissions allowing it to function further without interacting with user. Then it can connect to C2 server to receive various commands and perform overlay attacks. Threat operators can issue a no. of commands for various operations such as logging keystrokes, spamming the victims' contact lists with text messages, setting the malware as the default SMS manager, pushing system notifications to the C2 server, locking the victim in the device home screen; and steal and hide notifications, send, spam and steal SMS messages and many more.
Also, BlackRock redirects the victim to Home screen if he/she tries to start or use specific Antivirus software. The malware has capability to deflect majority of mobile Antivirus applications installed on device.
Another feature of this android Trojan is making use of “Android work profiles” to control the compromised device without requiring complete admin rights, instead creating and attributing its own managed profile to gain admin privileges.
Infection mechanism:
Package name:
- ayxzygxgagiqhdnjnfduerzbeh.hme.egybgkeziplb
- cmbmpqod.bfrtuduawoyhr.mlmrncmjbdecuc
- fpjwhqsl.dzpycoeasyhs.cwnporwocambskrxcxiug
- onpekpikylb.bcgdhxgzwd.dzlecjglpigjuc
- ezmjhdiumgiyhfjdp.bjucshsqxhkigwyqqma.gqncehdcknrtcekingi
SHA 256 Hahses:
- 51f9c37c3eec0b6f8325aa1c8fe64a0615ab920584042df557426473b1270b40
- 6fa4baef8a811f429cee4b383d7a4776b7b363b62551c8d8e0f93bad33adefbd
- 7d34aaf84754fb247507681bcd821f9533f24c6d78aa6779a11f4d789d4822ee
- 81fda9ff99aec1b6f7b328652e330d304fb18ee74e0dbd0b759acb24e7523d8c
- fbaf785edfafa583ea61884d88f507a27154892a394e27d81102f79fe7eb5b8f
Countermeasures and Best practices for prevention:
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages]. Install applications downloaded from reputed application market only.
- Install and maintain updated antivirus solution on android devices. Scan the suspected device with antivirus solutions to detect and clean infections.
- Prior to downloading / installing apps on android devices (even from Google Play Store), Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- In settings, do not enable installation of apps from "Untrusted Sources".
- Exercise caution while visiting trusted/untrusted sites for clicking links.
- Install Android updates and patches as and when available from Android device vendors.
- Users are advised to use device encryption or encrypting external SD card feature available with most of the android OS.
- Do not download or open attachment in emails received from untrusted sources or unexpectedly received from trusted users.
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
- Confirm that the banking/financial app you’re using is the official, verified version.
- If anything looks awry or suddenly unfamiliar, check in with your bank’s/financial service provider's customer service team.
- Use two-factor authentication if it’s available.
- Make sure you have a strong AI-powered mobile antivirus installed to detect and block this kind of tricky malware if it ever makes its way onto your system.
- Refer to security best practices for mobile Phone users:
http://www.cyberswachhtakendra.gov.in/documents/Mobile_phone_Security.pdf
References:


