Android Banker Trojan
Original Issue Date:-
January 04, 2018
Type:-
Banking Trojan
Severity:-
Medium
It has been reported that a malicious application targeting various banking and payment apps [including Indian banks] has been circulating. The malicious application is masquerading as Flash Player which is being offered via third party app stores, possibly when the users are being directed from compromised servers or after clicking on ads. The application is instructed to steal banking credentials, intercept SMSs, displaying an overlay screen (to capture details) on top of legitimate apps,steal sensitive data to attacker controlled servers, among others.
Note:
Adobe Flash player is in-built in Android Mobile browsers since Android Version 4.1 and official versions are not being offered for download in Google Play.
Once successfully installed via side-loading and being granted administrative privileges on the system, it listens for command from the c2 server and keeps track of the installed applications. If the targeted payment applications [the complete list can be seen from the link in the reference section] found, the app shows a fake notification on behalf of the targeted banking app with the app’s icon. If the user clicks on the notification leads to a phishing page of the targeted bank to steal the user’s confidential.
Up on receiving specific commands from the C2 server, the app can do activities in the background like intercept SMS’s to thwart OTP based authentication, can collect all the contacts and SMS on the device and siphon off to the C2 server, can send specific SMS on the mobile contacts, can send IP/GPS location etc.
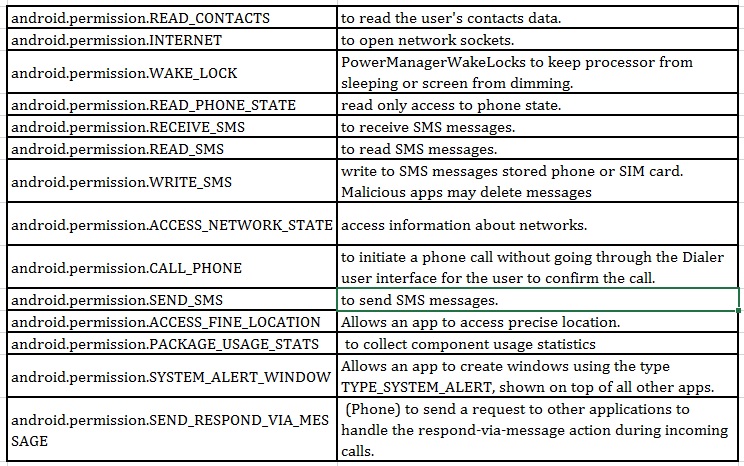
The malware requests the following permissions while installing.
Best Practices
- Do not download and install applications from untrusted sources [offered via unknown websites/ links on unscrupulous messages].Install applications downloaded from reputed application market only.
- Prior to downloading / installing apps on android devices (even from Google Play Store):
- Always review the app details, number of downloads, user reviews, comments and "ADDITIONAL INFORMATION" section.
- Verify app permissions and grant only those permissions which have relevant context for the app's purpose.
- Do not check "Untrusted Sources" checkbox to install side loaded apps.
- Exercise caution while visiting trusted/untrusted sites for clicking links.
- Install and maintain updated antivirus solution on android devices. Scan the suspected device with antivirus solutions to detect and clean infections.
- Refer to security best practices for mobile Phone users:
http://www.cyberswachhtakendra.gov.in/documents/Mobile_phone_Security.pdf - Install Android updates and patches as and when available from Android device vendors
- Enable 2-factor authentication for your Google/other accounts.
- Users are advised to use device encryption or encrypting external SD card feature available with most of the android OS
- Avoid using unsecured, unknown Wi-Fi networks. There may be rogue Wi-Fi access points at public places used for distributing malicious applications.
References
- http://blogs.quickheal.com/android-banking-trojan-targets-232-apps-including-indian-banks/
- https://www.virustotal.com/en/file/40ad2444b83f6a1c25dd153214a1a16bcaa2640ebaf7735d6f1ee2591989e58e/analysis/


